Events 
Upcoming
2026-02-25
Lecture
Lecture by Nataliia Bielova (Inria) “Regulating Consent and Dark Patterns: Bridging Law, Web Measurement, and HCI“
Location: TU Wien, FAV Hörsaal 3 Zemanek (Favoritenstraße 9-11, 1040 Wien) (HHEG01)(https://maps.tuwien.ac.at/?q=HHEG01 )) Virtual location: https://live.video.tuwien.ac.at/watch?l=iwWhYq1fWmHBcESTpTboSa
Time: 11:00 ‒ 12:00
Abstract: Over the past decades, Web tracking technologies have enabled pervasive, large-scale surveillance of online activity for data extraction and targeted advertising. In response, European regulators have sought to safeguard users through the consent required by the General Data Protection Regulation (GDPR), operationalized in practice via cookie consent banners. Yet these interfaces frequently rely on “dark patterns” that manipulate user decision-making. Such manipulative design does not only affect end users, but can also distort interactions among other actors in the web ecosystem.
In this talk, I examine how cookie consent mechanisms and dark patterns can be regulated under existing and emerging EU legal frameworks, including the General Data Protection Regulation and the Digital Services Act (DSA). I argue that effective enforcement requires close collaboration between legal scholars, web measurement researchers, and the HCI community. By combining doctrinal legal analysis with web measurements and empirical user studies, regulators can be better equipped to make robust, evidence-based, legally binding decisions. I conclude by outlining the key opportunities and methodological challenges of this emerging transdisciplinary research agenda aimed at strengthening user protection online.
Bio: Dr. Nataliia Bielova is a Research Director in Computer Science at Inria (French Institute for Research in Computer Science and Automation). She is a privacy expert with a multidisciplinary background in computer science and regulation, investigating privacy and data protection on the Web. Dr. Bielova was a Senior Privacy Fellow at the French Data Protection Authority (CNIL) and an External Expert for the EU Commission for its implementation of the EU Digital Services Act (DSA). She received a Young Researcher Award from the French National Research Agency (ANR), the Rising Star award by Women at Privacy in 2023, the CNIL-Inria Privacy Award in 2025 and the Lovelace-Babbage Award from the French Science Academy and the French Computer Society in 2025.
January 2026
2026-01-28
Lecture
Lecture by Petia Niederlaender (Austrian National Bank) “Digital Euro and Beyond - CBDCs and Stablecoins in Europe“
Location: TU Wien, EI 8 Pötzl HS (Gußhausstraße 27-29, 1040 Wien, CDEG08 )
2026-01-26
Lecture
Сolloquium presentation
by Laura Kovács at Lorraine Research Laboratory in Computer Science and its Applications (Loria)
Topic: Induction and synthesis in saturation-based theorem proving
Abstract: Proof by induction is commonplace in mathematics. logic, formal verification, cybersecurity, and many more areas. This talk overviews recent progress in automating inductive reasoning in saturation-based first-order theorem proving We formalize applications of induction as new inference rules of the saturation process, add instances of appropriate induction schemata to the search space, and use these rules and instances immediately upon their addition for the purpose of guiding induction. We also synthesize code that satisfies a given (inductive) logical specification, while proving the specification in a saturation-based framework.
2026-01-14
Research Visit
Lecture by Fabian Yamaguchi (Whirly Labs, Stellenbosch University) “Automations for Zero-Day Vulnerability Discovery“
Location: TU Wien, EI 11 Geodäsie HS (Gußhausstraße 27-29, 1040 Wien, CD0304 )
Virtual location: https://tuwien.zoom.us/j/68970632137
Time: 14:00 ‒ 16:00
Abstract: The discovery of zero-day vulnerabilities remains one of the most significant challenges in computer security, traditionally reliant on the manual expertise of seasoned security researchers. As software complexity scales exponentially, manual auditing alone can no longer keep pace with the vast attack surfaces of modern codebases. This lecture explores the evolution of automated vulnerability discovery, centering on the development and application of the Code Property Graph (CPG) - a unified program representation that has bridged the gap between academic static analysis and industrial-scale security auditing.
We will begin by examining the theoretical foundations of the CPG, which merges abstract syntax trees (ASTs), control flow graphs (CFGs), and program dependence graphs (PDGs) into a single, queryable data structure. This representation allows for the elegant modeling of complex vulnerability patterns — such as taint-style flaws and missing checks — using expressive graph traversals.
Moving from theory to practice, the session will detail the challenges and “street smarts” required to implement these concepts in a production environment. Drawing on experience from the open-source platform Joern and its commercial counterparts, we will discuss:
- Scalability: How to perform deep data-flow tracking across millions of lines of code within modern CI/CD time constraints (e.g., < 10 minutes).
- Abstraction Levels: Handling diverse instruction sets and programming languages through a language-agnostic intermediate representation.
- Human-in-the-Loop Automation: Shifting the focus from “black-box” scanners to extensible “analyst workbench” tools that augment the auditor’s capabilities.
The lecture concludes with a look at the future of the field, including the integration of machine learning and large language models (LLMs) with graph-based analysis to further refine the precision of automated bug hunting.
Bio: Prof. Dr. Fabian Yamaguchi is co-founder and CTO of Whirly Labs, Adjunct Professor for Computer Security at Stellenbosch University, and Chief Scientist Emeritus at Qwiet.ai (formerly ShiftLeft Inc.). He is a seasoned expert in cyber security with over 20 years of experience, both as an individual contributor and in leadership roles.
Most recently, he was a founding team member of ShiftLeft Inc where he built and led the R&D team that designed and implemented the technology for automated vulnerability discovery at the heart of the product offering - based on his 2015 award-winning PhD thesis “Pattern-Based Vulnerability Discovery”.
Throughout his career, he has identified previously unknown vulnerabilities in widely used software such as Microsoft Windows and Linux kernels, the Squid proxy server, and the VLC media player. He has presented his findings and techniques at both major industry conferences such as BlackHat USA, DefCon, First, and CCC, and renowned academic security conferences such as ACSAC, IEEE Security and Privacy, and CCS.
He is the inventor of the code property graph and lead developer of the open-source code analysis platform Joern. Fabian holds a PhD in computer science from the University of Goettingen and a master’s degree in computer engineering from Technical University Berlin.
December 2025
2025-12-15
Research Seminar
Memory Band-Aid: A Principled Rowhammer Defense-in-Depth
Speaker - Carina Fiedler (TU Graz)
2025-12-01
Lecture
Daniel Gruss is a speaker at the International Winter School on Microarchitectural Security (MIC-SEC 2025
)
November 2025
2025-11-24
Research Seminar
Space-Deniable Proofs
TU Wien will host Krzysztof Pietrzak and Christoph Ullrich Günther (ISTA) for a research visit. The agenda includes technical discussions on current projects and a planned talk. The visit aims to strengthen collaboration between ISTA and TU Wien.
Speaker - Christoph Ullrich Günther (ISTA)
Abstract: We introduce and construct a new proof system called Non-interactive Arguments of Knowledge or Space (NArKoS), where a space bounded prover can convince a verifier they know a secret, while having access to sufficient space allows one to forge indistinguishable proofs without the secret.
An application of NArKoS are space-deniable proofs, which are proofs of knowledge (say for authentication in access control) that are sound when executed by a lightweight device like a smart-card or an RFID chip that cannot have much storage, but are deniable (in the strong sense of online deniability) as the verifier, like a card reader, can efficiently forge such proofs.
We construct NArKoS in the random oracle model using an OR-proof combining a sigma protocol (for the proof of knowledge of the secret) with a new proof system called simulatable Proof of Transient Space (simPoTS). We give two different constructions of simPoTS, one based on labelling graphs with high pebbling complexity, a technique used in the construction of memory-hard functions and proofs of space, and a more practical construction based on the verifiable space-hard functions from TCC'24 where a prover must compute a root of a sparse polynomial. In both cases, the main challenge is making the proofs efficiently simulatable.
2025-11-18
Research Visit
Lecture by Kazuki Watanabe (National Institute of Informatics, Japan) “A String Diagrammatic Approach to Structural Verification“
Location: TU Wien, EI 8 Pötzl HS (Gußhausstraße 27-29, 1040 Wien, CDEG08
)
Time: 11:00 ‒ 12:00
Abstract: We present a string diagrammatic approach to structural (modular or compositional) verification. In this talk, we focus on probabilistic model checking of Markov decision processes and we show compositional algorithms that leverage multi-objective optimization. Finally, we introduce our ongoing work that extends this approach. This talk is based on joint work with Kazuyuki Asada, Clovis Eberhart, Ichiro Hasuo, Sebastian Junges, Satoshi Kura, Jurriaan Rot, Hiroshi Unno, and Marck van der Vegt.
Bio: Kazuki Watanabe is an Assistant Professor at the National Institute of Informatics (NII), Japan. He received his Ph.D. in Informatics from NII in March 2025 under the supervision of Professor Ichiro Hasuo. In 2023, he spent six months at Radboud University as a guest hosted by Professors Jurriaan Rot and Sebastian Junges. His research focuses on applied category theory and algorithms for formal verification.
2025-11-11
Research Visit
Lecture by Gianluca Stringhini (Boston University) “LLMs for Software Vulnerability Detection: Holy Grail, Pandor`s Box, or just a Fad?“
Location: TU Wien, FAV Hörsaal 2 (Favoritenstraße 9-11, Erdgeschoß, HEEG03
)
Virtual Location: https://tuwien.zoom.us/j/66595171033
Time: 11:00 ‒ 12:00
Abstract: In this talk, I will discuss the results of our investigation on the ability of Large Language Models (LLMs) to detect software vulnerabilities. I will show that while LLMs show promise, they present several pitfalls like non-determinism in their outputs and unfaithful reasoning. I will then talk about how we can manage these pitfalls to create an agentic framework that is able to take CVEs of known vulnerabilities, set up a working environment with the vulnerable software, and produce a verifiable exploit against the vulnerability. This framework allows the research community to produce benchmarks of known vulnerabilities and their exploits, which are needed to test new defenses. Unfortunately, our framework also shows that automated generation of exploits using LLMs is a real threat that could be weaponized by attackers. I will finally conclude discussing the future challenges and opportunities of LLMs for vulnerability detection.
Bio: Gianluca Stringhini is an Associate Professor in the Electrical and Computer Engineering Department at Boston University, holding affiliate appointments in the Computer Science Department and in the Faculty of Computing and Data Sciences. In his research Gianluca applies a data-driven approach to better understand malicious activity on the Internet. Through the collection and analysis of large-scale datasets, he develops novel and robust mitigation techniques to make the Internet a safer place. Over the years, Gianluca has worked on understanding and mitigating malicious activities like malware, software vulnerabilities, online fraud, influence operations, and coordinated online harassment. He received multiple prizes including an NSF CAREER Award in 2020, and his research won multiple Best Paper Awards. Gianluca has published over 150 peer reviewed papers including several in top computer security conferences like IEEE Security and Privacy, CCS, NDSS, and USENIX Security, as well as top measurement, HCI, and Web conferences such as IMC, ICWSM, CHI, CSCW, and WWW.
2025-11-07
Award
2025 Research Promotion Award of the Government of Styria
Prof. Maria Eichlseder received the Förderungspreis des Landes Steiermark 2025 for her work on “Secure Lightweight Cryptography.” The prize, awarded by the Styrian Science and Research Councillor Willibald Ehrenhöfer in the White Hall of Graz Castle, honours outstanding achievements by researchers under 40.
In her award-winning work, Eichlseder advances the foundations of modern cryptography, which underpins secure communication, data integrity and privacy protection in democratic societies. A key focus is lightweight cryptography for constrained devices such as those in the Internet of Things. Her contributions include the design of the Ascon algorithm family, recently selected by the U.S. National Institute of Standards and Technology (NIST) as the new international standard for lightweight cryptography, as well as new techniques for precise, computer-aided cryptanalysis and for defending against physical fault attacks. These results are already influencing the state of the art and will help to better protect countless devices and sensitive data worldwide.
© Foto Fischer
2025-11-03
Lecture
Stefan Mangard delivered a Colloquium Talk
at the IITB Trust Lab (Indian Institute of Technology Bombay)
Title: How Hardware Helps and Hurts Software Security.
Abstract: In recent years, hardware has made significant strides in supporting isolation of different security contexts. At the same time, advances in side-channel attacks have shown that even strong isolation mechanisms can be undermined through physical, microarchitectural, and software-level effects. This talk explores selected recent research on how hardware mechanisms can strengthen software isolation and how side-channel attacks, at the same time, can erode such boundaries.
2025-11-03
Public Lecture
Krzysztof Pietrzak delivered a research talk
The talk is a part of the Public Lecture Series ‘Sustainability in Computer Science’ under the auspices of Informatik Austria .
Abstract. The Bitcoin blockchain achieves consensus in an open setting, i.e., where everyone can participate. This was believed to be impossible, the key idea to make this possible was to use computing power rather than some kind of identities for voting through “proofs of work”. Unfortunately, this approach is not sustainable: the Bitcoin blockchain burns roughly as much electricity as a country like Austria. We will outline sustainable alternatives for achieving a Bitcoin-like blockchain, with a focus on using disk space instead of computation and how this is realized in the Chia Network blockchain.
October 2025
2025-10-30
Research Visit
Lecture by Mugdha Khedkar (Paderborn University, Germany) “Static Analysis for Android GDPR Compliance Assurance“
Location: TU Wien, Seminarraum FAV 05 (Seminarraum 186, Favoritenstraße 9-11, Obergeschoß, HA0503
)
Virtual Location: https://tuwien.zoom.us/j/63435768500
Time: 11:00 ‒ 12:00
Abstract: Android applications collecting data from users must protect it according to the current legal frameworks. This need for data protection has become even more crucial with the introduction of the General Data Protection Act (GDPR) by the European Union. While many Android applications state a privacy policy, privacy assessments are manual and thus very costly and error prone. A major challenge lies in bridging the gap between legal privacy statements (written in natural language) and the technical measures implemented within apps. In this talk, I will discuss how static program analysis can help address key data protection challenges and support GDPR-compliant documentation. Our goal is to develop automated, static analysis-based approaches that improve understanding and enhance collaboration between app developers, privacy professionals, and legal experts, ultimately ensuring stronger data protection in Android applications.
Bio: Mugdha Khedkar is a final-year PhD student in the Secure Software Engineering Group at Paderborn University, Germany, where she works with Prof. Dr. Eric Bodden. Her research interests include an intersection of program analysis, data protection, and empirical software engineering. She earned her Master’s degree in Computer Science from the Chennai Mathematical Institute, India. Outside academia, she enjoys traveling and writing, and brings these interests together in her travel blog.
2025-10-22
Research Visit
Lecture by Diego Olivier Fernandez Pons (Microsoft) “MIP Engines are Saturation Engines Too“
Location: TU Wien, FAV Hörsaal 3 Zemanek (Seminarraum Zemanek, Favoritenstraße 9-11, Erdgeschoß, HHEG01
)
Time: 15:00 ‒ 16:00
Virtual Location: https://live.video.tuwien.ac.at/watch?l=4ns5B5mJYMrWJb7n3W958g
Abstract: Saturation-based theorem provers use heuristics to create and delete formulas. Mixed integer programming engines used in mathematical optimization, while based on DPLL, also are saturation-based theorem provers for systems of integer linear equations. The algorithm that guides and supports the formula generation is the LP while the formulas are generated by the cutting-planes heuristics in a process globally known as the separation problem. We will show the similarities and differences between saturation-based theorem provers and MIP engines, and try to identify research directions that could benefit both communities.
Bio: Diego Olivier Fernandez Pons started his career in ILOG R&D working on MIP and Constraint Programming engines. Then worked for IBM as an optimization consultant. He is the co-author of OptalCP a constraint programming engine for scheduling problems. And he works today in the quantum group of Microsoft.
2025-10-16
Presentation
Ivana Bocevska presented at ICFP/SPLASH 2025
Ivana Bocevska presented at “Divide and Conquer: A Compositional Approach to Game-Theoretic Security ,” coauthored with Anja Petković Komel, Laura Kovács, Sophie Rain, and Michael Rawson. They propose a compositional approach to combine and scale automated reasoning for the static analysis of decentralized systems such as blockchains. The method models protocols as games driven by economic incentives and proves that honest behavior is never disadvantageous, regardless of others’ actions. Instead of verifying one monolithic model that cannot scale to millions of interactions, the authors decompose the overall game into smaller subgames, analyze each, and then compose the results; when a component changes, only that part and its ancestors need to be rechecked. The approach is sound and complete, uncovers properties and bugs in large protocols, and makes rigorous, incentive-aware security proofs practical at real-world scale.
2025-10-15
Lecture
Laura Kovács is an invited speaker at the DynAMiCs workshop
The workshop “Algebraic Methods in Dynamics and Particle Physics ”, organized by the Max Planck Institute for Software Systems (MPI-SWS) with support from the Max Planck Center for Particle Physics, Cosmology and Geometry and the Max Planck Center for Mathematics in the Sciences, brings together leading researchers in dynamics, algebra, and particle physics to explore themes at their intersection. Focus areas include the development of mathematical languages for describing physical phenomena across scales, as well as the algebraic and algorithmic foundations of discrete and continuous dynamical systems. Laura Kovács delivered the lecture “Algebraic Methods in Dynamics and Particle Physics ”.
Abstract: Despite the substantial progress in the computer-aided verification of computer systems, ensuring the correctness of programs implementing algebraic operations is still an open problem. This problem remains unsolved even when we restrict consideration to loops that are non-nested, without exit conditions, and/or only use limited (polynomial) arithmetic.Such programs naturally arise in compiler optimization, cryptography, cybersecurity, control theory, and probabilistic reasoning. This talk will present classes of computer systems for which we automatically can solve the challenge of proving programs error-free. Key to our setting is the combination of algebraic techniques with static code analysis, allowing us to even turn some unsolvable verification challenges into solvable ones.
2025-10-13
Research Seminar
Cryptanalysis of New Low-Latency Cipher Designs
Speaker - Simon Gerhalter (TU Graz)
2025-10-10
Research Visit
Lecture by Arkady Yerukhimovich (George Washington University) “Non-Interactive Verifiable Aggregation (NIVA)“
Location: TU Wien, FAV Hörsaal 3 Zemanek (Seminarraum Zemanek, Favoritenstraße 9-11, Erdgeschoß, HHEG01
)
Time: 11:00 ‒ 12:00
Virtual Location: https://live.video.tuwien.ac.at/watch?l=vjbu2jzbD2nBhHVaCEdEiZ
Abstract: Consider a weak analyst that wishes to outsource data collection and computation of aggregate statistics over a potentially large population of (also weak) clients to a powerful server. For flexibility and efficiency, we consider public-key and non-interactive protocols, meaning the clients know the analyst’s public key but do not share secrets, and each client sends at most one message. Furthermore, the final step should be silent, whereby the analyst simply downloads the (encrypted) result from the server when needed. To capture this setting, we define a new primitive we call Non-Interactive Verifiable Aggregation (NIVA). We require both privacy and robustness for a NIVA protocol to be deemed secure. Namely, our security notion for NIVA ensures that the clients’ data remains private to both the server and the analyst, while also ensuring that malicious clients cannot skew the results by providing faulty data.
We propose a secure NIVA protocol, which we call PEAR (for Private, Efficient, Accurate, Robust), which can validate inputs according to any NP validity rule. PEAR is based on a novel combination of functional encryption for inner-products (Abdalla et al., PKC 2015) and fully-linear probabilistically-checkable proofs (Boneh et al., Crypto 2019). We emphasize that PEAR is non-interactive, public-key, and makes black-box use of the underlying cryptographic primitives. Additionally, we implement PEAR and conduct a thorough performance evaluation showing improvement over prior work for practically-relevant validity rules.
Bio: Arkady Yerukhimovich is an associate professor of Computer Science at George Washington University. His research interests span theoretical and applied cryptography with a focus on building provably-secure protocols to enable people to communicate, search, and compute over their personal data while preserving their privacy. In particular, his recent research focuses on “large-scale” secure computation looking to perform secure computation with a large number of parties or on very large inputs. Prior to joining George Washington University, professor Yerukhimovich received his PhD from the University of Maryland where his research focused on black-box separations.
September 2025
2025-09-29
Research Seminar
Side-channel countermeasures for Post-quantum cryptography
Speaker - Rishub Nagpal (TU Graz)
2025-09-25
Mentoring
“Ask Me Anything” & Female Mentoring Session
SPyCoDe hosted a women’s mentoring session featuring Rachel Cummings and Kathrin Grosse, who shared candid insights from their studies, research, and career journeys. Participants gained practical advice on navigating academia and industry, and expanded their professional networks in a field that remains traditionally male-dominated. The session provided targeted support to help ease entry barriers and enable talented researchers to realize their full potential.
2025-09-22
Summer School
Summer School on Artificial Intelligence and Cybersecurity
The first Summer School on AI and Cybersecurity
will take place from 22 to 26 September 2025 at TU Wien. This premier, week-long event stands at the intersection of cutting-edge research and practical application, bringing together leading experts, researchers, and students from around the world to explore the transformative impact of artificial intelligence on modern cybersecurity.
Registration is now open at link
Take advantage of early-bird rates available until July 10, 2025.
2025-09-22
Lecture
Tom Henzinger is an invited speaker at SYNASC 2025
Prof. Tom Henzinger (ISTA) has been invited to speak at the 27th International Symposium on Symbolic and Numeric Algorithms for Scientific Computing (SYNASC 2025 ), to be held on September 22–25 in Timișoara, Romania. He will present a talk titled “Neural Certificates.” SYNASC brings together researchers from fields such as symbolic and numeric computation, formal methods, artificial intelligence, distributed computing, and computational theory, promoting collaboration on the development of complex, reliable, and high-performance computational systems. The event is organized by leading academic and research institutions from Romania and Austria.
Abstract: Symbolic datatypes are central to abstract reasoning about dynamical systems. Successful examples include BDDs and SAT for finite-state systems, and polyhedra and SMT for discrete dynamical systems over certain infinite state spaces. Neural networks provide a natural symbolic datatype over continuous state spaces, with the added benefit of supporting key operations while being trainable. We advocate using neural networks for multiple purposes in reasoning about continuous state spaces, particularly for representing both deterministic dynamics — such as controllers — and correctness certificates. A correctness certificate is a succinct witness for a desired property of a dynamical system. For example, invariants and barrier functions certify safety, while Lyapunov functions and supermartingales certify progress. Stochastic barrier functions and supermartingales can further account for uncertainty (noise) in system dynamics. Established techniques from machine learning and formal reasoning about neural networks — such as SMT, abstract interpretation, and counterexample-guided refinement — enable the joint synthesis of controllers and correctness certificates. This allows for the synthesis of guaranteed-to-be-correct controllers, where both the controllers and their certificates are represented, learned, and verified as neural networks. This talk includes joint work with Krishnendu Chatterjee, Mathias Lechner, and Djordje Zikelic.
2025-09-22
Defense
Ivana Bocevska (TU Wien) successfully defended her master’s thesis, “Extending Game-Theoretic Security of Blockchain Protocols with Compositional Reasoning and Conditional Actions.”
Her work advances the formal analysis of blockchain systems by combining game-theoretic security models with compositional methods to reason about complex protocol behavior.'
2025-09-22
Engagement Activities
17th Alpine Verification Meeting (AVM25)
Prof. Laura Kovács is the organizer of the 17th Alpine Verification Meeting (AVM’25 ), an informal meeting focused on verification, model checking, and abstract interpretation. Launched in 2005 in Lausanne, AVM brings together PhD students, postdocs, and senior researchers from across the Alpine region to share updates on ongoing work. The 2025 edition will take place in Timișoara, Romania, with Prof. Thomas A. Henzinger as invited speaker.
2025-09-18
Lecture
Laura Kovács is a keynote speaker at womENcourage™ 2025
The 12th ACM Celebration of Women in Computing (womENcourage ), which will be hosted by Transilvania University of Brașov on September 17–19, will explore the theme “Computer Science: a Catalyst for Educational Change”, focusing on how computing innovations will transform education, promote accessibility, and address ethical and cybersecurity challenges. This ACM‑W Europe initiative will celebrate women’s achievements in computing, fostering collaboration among students, researchers, and professionals to advance diversity, gender equality, and innovation in STEM.
2025-09-16
Research Visit
Lecture by Samuel Kopmann (Karlsruhe Institute of Technology) “Feedback-driven Autonomous Data Set Labeling for Denial-of-Service Attack Traffic“
Location: TU Wien, Seminarraum 1 (Institute of Telecommunications, Entrance CF, Gußhausstrasse, 25-25a, Erdgeschoß) (CG 0118
)
Time: 12:00 ‒ 13:00
Abstract: Expert-driven labeling of network traffic for Denial of Service (DoS) detection is error prone and prohibitively expensive in large-scale environments, such as Internet Service Provider (ISP) networks. However, supervised Machine Learning-based (ML) DoS detection approaches require high-quality and up-to-date training data sets. To ensure fast and high-quality data set creation for ML model training while facing evolving traffic patterns in the legitimate and the attack traffic, there is a need for a labeling approach without an expert in the loop. This presentation outlines FeADable, a retrospective and fully autonomous labeling approach that leverages autoencoders to distinguish between legitimate and attack traffic based on reported feedback about occurred attacks. FeADable enables the scalable labeling of application layer DoS attacks and volumetric Distributed DoS (DDoS) attacks with near-perfect precision and false-positive feedback resilience, which ensures fast retraining of deployed detection models in response to successful attacks. The presentation covers evaluation results of FeADable with authentic, real-world data sets that are publicly available, i.e., from the Canadian Institute for Cybersecurity, and with network traffic of a tier-1 ISP. I will further outline FeADable’s compatibility with different monitoring approaches, i.e., micro-flows and traffic aggregates, to emphasize its labeling capability of DoS traffic independent of the traffic representation
Bio: Samuel Kopmann has been working as a Research Assistant and Ph.D. candidate at the Institute of Telematics, Karlsruhe Institute of Technology since 2021. He is interested in the application of computer vision approaches to network traffic classification and developing novel approaches to overcome limited data availability for Machine Learning (ML) in networking. His research focuses on detecting and mitigating volumetric DDoS attacks with ML while maintaining fixed and predictable resource consumption, i.e., memory and CPU utilization.
2025-09-15
Lecture
Tom Henzinger is a keynote speaker at 25th International Conference on Runtime Verification (RV25
)
Title: How Hardware Helps and Hurts Software Security.
Abstract: Fairness in AI is traditionally studied as a static property evaluated once, over a fixed dataset. However, real-world AI systems operate sequentially, with outcomes and environments evolving over time. This paper proposes a framework for analysing fairness as a runtime property. Using a minimal yet expressive model based on sequences of coin tosses with possibly evolving biases, we study the problems of monitoring and enforcing fairness expressed in either toss outcomes or coin biases. Since there is no one-size-fits-all solution for either problem, we provide a summary of monitoring and enforcement strategies, parametrised by environment dynamics, prediction horizon, and confidence thresholds. For both problems, we present general results under simple or minimal assumptions. We survey existing solutions for the monitoring problem for Markovian and additive dynamics, and existing solutions for the enforcement problem in static settings with known dynamics.
2025-09-08
Lecture
Matteo Maffei is a speaker at The SERICS Summer School on Secure Software Development
Prof. Matteo Maffei delivered “Foundations of Secure Blockchain Programming,” surveying core risks in blockchain systems, including smart contract bugs, reentrancy, front-running, and flawed consensus design. He emphasized that immutability and transparency do not prevent implementation errors. He outlined secure coding practices such as formal verification, runtime checks, gas-cost awareness, and careful language and framework choices, and recommended tools and techniques including automated testing, fuzzing, static analysis, code audits, symbolic execution, and model checking.
2025-09-01
Lecture
Elena Andreeva is an invited speaker at the 1st Workshop on Generic Attacks and Proofs in Symmetric Cryptography
The 1st Workshop on Generic Attacks and Proofs in Symmetric Cryptography (GAPS 2025 ), held at NTU Singapore on September 1–5, 2025, gathered leading and early-career researchers in provable symmetric-key cryptography under the theme “Five Decades of Provable Security of Symmetric Ciphers: Challenges and Future Developments”. Prof. Elena Andreeva delivered an invited lecture on “Expanding the Scope, Security, and Efficiency of Classical Symmetric Primitives,” demonstrating how primitives such as ForkSkinny and Butterknife can exceed classical bounds, enhance robustness (e.g., nonce-reuse resilience, block-wise adaptive security), and improve performance across applications in authenticated encryption, key derivation, IoT security, cloud decryption, and message authentication. She highlighted the flexibility and efficiency of such designs and outlined promising directions for future research.
2025-09-01 Summer School
The Graz Security Week 2025 will take place at the Institute of Applied Information Processing and Communication (IAIK) at Graz University of Technology. This renowned cybersecurity summer school is designed for graduate students with an interest in security, privacy, and system correctness.
This year’s program will focus on key topics such as Cryptography & Cryptographic Implementations, Side Channels Privacy, and Safe AI. The full program is now available, and registration is open. Interested participants are encouraged to secure their spot here.
The event will feature lectures and workshops from leading experts in the field, including:
- Sahar Abdelnabi, Microsoft
- Jo Van Bulck, KU Leuven
- Maria Eichlseder, TU Graz
- Georg Fuchsbauer, TU Wien
- Daniel Gruss, TU Graz
- David Oswald, University of Birmingham
- Fabio Pierazzi, University College London
- Kaveh Razavi, ETH Zürich
- Christian Rossow, CISPA
- Yang Zhang, CISPA
For more details, visit the official program here . Join us!
August 2025
2025-08-27
Research Visit
Lecture by Joël Ouaknine (Max Planck Institute for Software Systems) “Fragments of Hilbert’s Program“
Location: TU Wien, FAV Hörsaal 1 Helmut Veith - INF (Favoritenstraße 9-11, Erdgeschoß) (HEEG02
)
Time: 11:00 ‒ 12:00
Abstract: Hilbert’s dream of mechanising all of mathematics was dealt fatal blows by Gödel, Church, and Turing in the 1930s, almost a hundred years ago. Paradoxically, assisted and automated theorem proving have never been as popular as they are today! Motivated by algorithmic problems in discrete dynamics, non-linear arithmetic, and program analysis, we examine the decidability of various logical theories over the natural numbers, and discuss a range of open questions at the intersection of logic, automata theory, and number theory.
Bio: Joël Ouaknine is a Scientific Director at the Max Planck Institute for Software Systems in Saarbrücken, Germany, where he leads the Foundations of Algorithmic Verification group. He also holds secondary appointments as Professor of Computer Science at Saarland University and as Emmy Network Fellow at Keble College, Oxford University. His research interests straddle theoretical computer science and mathematics, and lie mainly at the confluence of dynamical systems and computation, making use of tools from number theory, Diophantine geometry, algebraic geometry, and mathematical logic. Other interests include the algorithmic analysis of real-time, probabilistic, and infinite-state systems (e.g. model-checking algorithms, synthesis problems, complexity), logic and applications to verification, automated software analysis, and concurrency.
2025-08-25
Research Visit
Lecture by Niklas Metzger (Max Planck Institute for Software Systems) “Synthesis and Verification of Distributed Systems with Information Flow and Knowledge“
Location: TU Wien, Seminarraum FAV 01 C (Favoritenstraße 11) (HE0108
)
Time: 15:00 ‒ 16:00
Abstract: In this talk, we show how we leverage information flow and knowledge, two core hyperproperties in the security and verification of distributed systems, to guarantee the correctness of distributed systems via synthesis, model-checking, and monitoring. Traditionally, these notions appear only as requirements: security constrains information flow, and agents act based on what they know. Here, we first use them as design principles for the compositional synthesis of distributed systems. For distributed synthesis, whose goal is to automatically build component implementations that jointly satisfy a specification, we introduce explicit assumptions about the necessary information flow between components. These assumptions enable a decomposition into subproblems whose local solutions compose into a globally correct system. We then proceed toward verifying complex second-order hyperproperties, properties that require quantification over sets of traces, such as common knowledge and asynchronous hyperproperties. We introduce Hyper2LTL, an extension of existing temporal hyperlogics capable of expressing such second-order hyperproperties, together with an automata-based model-checking algorithm and a monitoring algorithm that verify whether a distributed system satisfies a given second-order hyperproperty.
Bio: Niklas Metzger is a Ph.D. student at the CISPA Helmholtz Center for Information Security and Saarland University. His research interests include hyperproperties, reactive synthesis, and the interplay of formal methods and machine learning. His current work focuses on compositional synthesis guided by the principles of knowledge, actual causality for reactive systems, and the use of machine learning models as heuristics in complex formal methods tasks.
2025-08-06
Lecture
Prof. Laura Kovács is a co-director and lecturer at the Marktoberdorf Summer School 2025
The Marktoberdorf Summer School 2025 on Specification and Verification for Secure Cyberspace (MOD25
) will focus on the latest advances in the specification and verification of secure, trustworthy cyberspaces. The program will offer 12 in-depth courses delivered by leading international researchers in the field, providing participants with a unique opportunity to engage with cutting-edge topics and methodologies.
Laura Kovács will deliver a mini-lecture series that presents the theory and practice behind the development of powerful theorem proving tools.
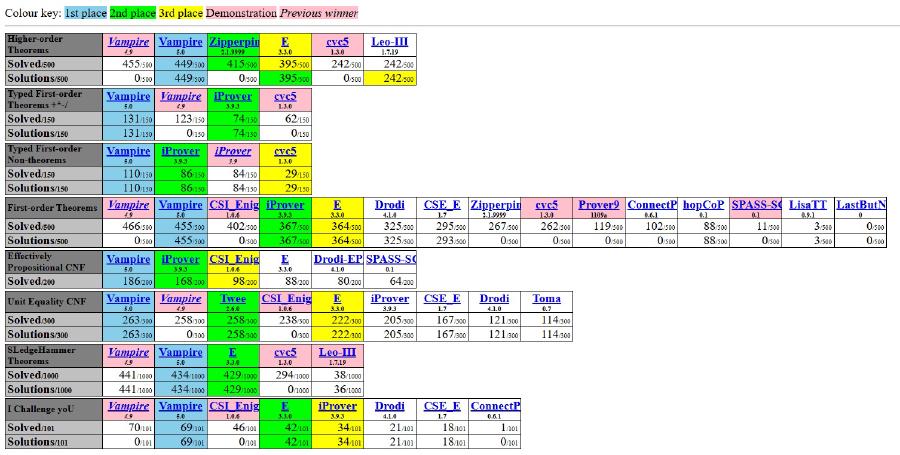
Topic: First-Order Theorem Proving and Vampire
Abstract: First-order theorem proving is one of the earliest research areas within artificial intelligence and formal methods. It is undergoing a rapid development thanks to its successful use in program analysis and verification, security analysis, symbolic computation, theorem proving in mathematics, and other related areas. Breakthrough results in all areas of theorem proving have been obtained, including improvements in theory, implementation, and the development of powerful theorem proving tools. However, recent developments are not always easily accessible to non-specialists.
The lectures will first focus on practicalities while using first-order Vampire for validating mathematical theorems. We will then further introduce the core concepts of automating first-order theorem proving in first-order logic with equality. We will discuss the resolution and superposition calculus, introduce the saturation principle, present various algorithms implementing redundancy elimination, and demonstrate how these concepts are implemented in Vampire.
July 2025
2025-07-24
Keynote
Roderick Bloem is a keynote speaker
at the 37th International Conference on Computer Aided Verification (CAV 2025)
At the upcoming 37th International Conference on Computer Aided Verification (CAV 2025) in Zagreb, Prof. Roderick Bloem (Graz University of Technology) will deliver a keynote titled “Side Channel Secure Software: A Hardware Question.”
Abstract: We will present a method to prove the absence of power side channels in systems that are protected using masking. Power side channels may allow attackers to discover secret information by measuring electromagnetic emanations from a chip. Masking is a countermeasure to hide secrets by duplication and addition of randomness. We will discuss how to formally prove security against power side channel techniques for circuits. We will then move on to software running on a CPU, where hardware details can have surprising effects. We will present some vulnerabilities on a small CPU and how to fix them, and we will talk about contracts that take side channels into account.
2025-07-21
Lecture
Tom Henzinger is an invited speaker at HYPER 2025
Prof. Tom Henzinger (ISTA, Austria) was invited to speak at HYPER 2025 – the 4th Workshop on Hyperproperties: Advances in Theory and Applications, scheduled for July 21, 2025, in Zagreb, Croatia, as part of CAV 2025. The goal of this workshop is to foster the exchange of ideas on the topic of hyperproperties between researchers from these diverse communities and to present and discuss recent advances in formalisms and methods for specifying and analyzing hyperproperties.
Title: First-Order Thoughts on Hyperproperties
Abstract: We look at hyperproperties from first principles using explicit quantification over two sorts - traces and time. Different quantifier orders expose semantic nuances concerning the synchronization of traces (or lack thereof). Trace quantifiers can be further distinguished to range over the traces of a model, or over the universe of all possible traces. This distinction allows the construction of unseen witness (or Skolem) traces when monitoring hyperproperties.
2025-07-21
Award
Vampire theorem prover achieves historic victory at CAV 2025 and CASC
At the flagship International Conference on Computer Aided Verification (CAV 2025 ), Vampire was honored with the Distinguished Paper Award for its latest tool presentation The Vampire Diary .
The SPyCoDe/TU Wien authors of the paper are Robin Coutelier, Laura Kovacs, and Johannes Schoisswohl. Their work presents the decade-long evolution of Vampire into a powerful automated solver for the combined theories of commonly used data structures, now including support for arithmetic, induction, and higher-order logic.
Simultaneously, Vampire made history at the annual CADE ATP System Competition (CASC ) - the premier competition for automated theorem provers - by winning all eight theorem proving divisions. This marks the first time in CASC history that a single prover has swept every division. Even more impressively, Vampire solved more problems than all other provers combined.
Over the past decade of continuous development, Vampire has matured into a versatile reasoning engine capable of effectively complementing SAT/SMT solvers and assisting proof assistants in software verification tasks. Its ongoing development is guided by strong engineering principles and carefully considered design choices, ensuring it continues to meet the evolving demands of formal verification.
2025-07-09
Presentation
SPyCoDe Members Play Key Role at DIMVA 2025 in Graz
The SPyCoDe research group played an active role in organizing and hosting the 22nd Conference on Detection of Intrusions and Malware & Vulnerability Assessment (DIMVA’25 ), held from July 9 to 11, 2025, in Graz, Austria.
Daniel Gruss served as General Chair and member of the Steering Committee, while Martina Lindorfer chaired Session 3: Side Channels. Daniel Gruss, Johanna Ullrich, and Martina Lindorfer contributed as Program Committee members, helping shape the conference’s technical program.
The team also presented groundbreaking research results:
The HMB Timing Side Channel: Exploiting the SSD’s Host Memory Buffer
Jonas Juffinger, Hannes Weissteiner, Thomas Steinbauer, Daniel Gruss (TU Graz)
This work introduces a novel cache side-channel attack targeting the Host Memory Buffer (HMB) of mid-range SSDs. The attack achieves eviction speeds of just 22 ms, enabling high-bandwidth covert channels (up to 8.3 kbit/s), UI redress attacks within 100 ms, blind templating, and cross-VM data exfiltration - even from processes without direct network access.
Cohere+Reload: Re-Enabling High-Resolution Cache Attacks on AMD SEV-SNP
Lukas Giner, S. R. Neela, Daniel Gruss (TU Graz)
This research uncovers new information leaks in AMD SEV-SNP’s encrypted memory coherence mechanism. Exploiting these leaks enables attackers to recover sensitive data with striking accuracy - including 99.7% of RSA key bits in a single trace and 100% AES key recovery in just 1,500 encryptions. The findings call for a re-evaluation of AMD’s coherence approach and further mitigation strategies.
2025-07-07
Defense
Jonas Juffinger (Graz University of Technology) successfully defended his PhD thesis
titled “Attacking and Securing Leaky Systems at the Hardware-Software Boundary”
The doctoral research, supervised by Prof. Daniel Gruss (Graz University of Technology) and Prof. Onur Mutlu (ETH Zurich, Switzerland), investigates vulnerabilities at the hardware-software boundary in modern computing systems. It focuses on side-channel and fault attacks that exploit hardware behaviors to leak sensitive information or gain unauthorized access. The thesis advances understanding of DRAM disturbance attacks (like Rowhammer), including their persistence and potential on SSDs, and proposes a robust hardware-software co-designed mitigation strategy. Additionally, it introduces the first side-channel analyses on commercial SSDs, revealing new software-based timing attacks. The research emphasizes the need for principled, generalizable defenses and includes peer-reviewed publications that contribute to the state of the art.
2025-07-04
Research Visit
Lecture by Sharad Agarwal (University College London) “Click, Reply, Lose: Understanding How Scammers Lure Users into Smishing Attacks“
Location: TU Wien, FAV Hörsaal 3 Zemanek (Seminarraum Zemanek, Favoritenstraße 9-11, Erdgeschoß) (HEEG02
)
Virtual Location: https://live.video.tuwien.ac.at/watch?l=7FLmRRZQm2Bta4GHCLWYiR
Time: 11:00 ‒ 12:00
Abstract: Recently, there has been a surge in SMS scams affecting users globally. Scammers send text messages impersonating well-known brands or individuals, luring victims into clicking malicious URLs, calling fraudulent phone numbers, or replying via text or email. In this talk, I present findings from my PhD research, which provides a comprehensive categorization of SMS scams and an in-depth analysis of two major types: the Hi Mum and Dad scam (a conversational scam) and delivery scams (URL-based smishing). While conversational scams often lead to Authorized Push Payment (APP) fraud, URL-based smishing scams typically result in unauthorized fraud, such as Card-Not-Present (CNP) fraud. The outcomes of these three research projects have been published or accepted at ACM IMC 2024, USENIX Security 2025, and NSPW 2025, respectively.
Bio: Sharad Agarwal is a final-year PhD candidate at University College London (UCL), where he specializes in combating online financial fraud. He studies cybercrime longitudinally using a data-driven approach. His research has been published at top academic venues like USENIX Security and Financial Cryptography and has been cited in major news outlets such as The Times. Alongside his Ph.D., he works as a Product Analyst at Stop Scams UK, helping translate research into real-world impact.
June 2025
2025-06-30
Presentation
Magdalena Steinböck delivered a presentation at 10th IEEE European Symposium on Security and Privacy (EuroS&P 2025)
At EuroS&P 2025 in Venice (June 30–July 4), Magdalena Steinböck presented the paper “SoK: Hardening Techniques in the Mobile Ecosystem – Are We There Yet? ”, co-authored with Martina Lindorfer and researchers from Vrije Universiteit Amsterdam and the University of Twente. The study introduced HALY, a framework for analyzing mobile app hardening, and evaluated 2,646 Android and iOS apps. Results showed that iOS apps lag significantly behind Android in adopting recommended protections, contradicting the assumption of iOS being inherently more secure. While most apps implement some safeguards, only a small fraction achieve full coverage, with reviewers recognizing HALY as the first large-scale comparative systematization of mobile hardening practices.
2025-06-23
Research Visit
Lecture by Geoff Sutcliffe (University of Miami) “The TPTP World - Infrastructure for Automated Reasoning“
Location: TU Wien, EI 2 Pichelmayer HS (Gußhausstraße 25-25a, 1040 Wien) (CF0235
)
Time: 13:00 ‒ 14:00
Abstract: The TPTP World is the established infrastructure used by the Automated Theorem Proving (ATP) community for research, development, and deployment of ATP systems. The data, standards, and services provided by the TPTP World have made it easy to develop, evaluate, and deploy ATP technology. This talk and tutorial reviews the core features of the TPTP World, describes key services of the TPTP World, and presents some successful applications. The use of ATP as the reliable substrate to subsymbolic AI systems (e.g., LLMs), to form neurosymbolic AI systems, is reviewed.
Bio: Geoff Sutcliffe is a Professor in the Department of Computer Science at the University of Miami. He received a BSc(Hons) and MSc from the University of Natal, and a PhD in Computer Science from the University of Western Australia. His research is in the area of Automated Theorem Proving (ATP), particularly in the evaluation and effective use of ATP systems. His most prominent achievements are the development and ongoing maintenance of the TPTP World, and the development and ongoing organization of the CADE ATP System Competition. He is one of the leaders of the StarExec project. His research has produced over 160 refereed journal, conference, and workshop papers.
2025-06-23
Presentation
Jonas Juffinger presented at the 23rd International Conference on Applied Cryptography and Network Security (ACNS 2025).
Jonas Juffinger and Sudheendra Raghav Neela presented the research paper “Not So Secure TSC ,” co-authored with Prof. Daniel Gruss (all from Graz University of Technology). The team explores a previously unexamined security challenge in modern cloud computing environments. Their work highlights how confidential virtual machines (VMs) - such as those secured using AMD SEV-SNP - remain vulnerable to co-location detection attacks, despite being designed for high-trust cloud scenarios. The researchers introduce the first co-location detection technique for confidential VM hosts, exploiting AMD’s SecureTSC feature. SecureTSC, intended as a tamper-resistant timing source, can be systematically abused to reveal whether two confidential VMs share the same physical hardware. The team developed a lightweight protocol, TsCupid, to detect co-location with high speed and minimal cost—achieving detection in as little as 0.13 seconds in parallelized scenarios. The study concludes by proposing a design-level mitigation to SecureTSC that could effectively prevent such attacks in future hardware generations. This work pushes the boundaries of cloud security research and underscores the urgent need for holistic security assessments of emerging trusted execution environments.
2025-06-13
Research Visit
Lecture by Christoph Kerschbaumer (Mozilla) “Towards a Secure and Privacy-Respecting Web“
Location: TU Graz, Lecture hall HS i1 (HSEG058J), Inffeldgasse 18, ground floor
Time: 11:00 ‒ 12:00
Abstract. The Hypertext Transfer Protocol, generally displayed as http in a browsers address-bar, is the fundamental protocol through which web browsers and websites communicate. However, data transferred by the regular http protocol is unprotected and transferred in cleartext, such that attackers are able to view, steal, or even tamper with the transmitted data. Carrying http over the Transport Layer Security (TLS) protocol, generally displayed as https in the address-bar of a browser, fixes this security shortcoming by creating a secure and encrypted connection between the browser and the website. Over the past few years we have witnessed tremendous progress towards migrating the web to rely on https instead of the outdated and insecure http protocol. Within this talk we will highlight initiatives from browser vendors as well as community efforts to accelerate the migration from http to https and explore additional privacy mechanisms within a web browser which eventually will provide a browsing experience we want: secure and privacy-respecting!
Bio: Dr. Christoph Kerschbaumer has over two decades of experience in software engineering and computer security. His work ranges from designing secure systems with fail-safe defaults to fighting cross-site scripting to preventing man-in-the-middle attacks. Currently he is managing the Firefox Security Engineering team at Mozilla and is mentoring software engineers around the world to reach their full potential. He received his PhD in Computer Science from the University of California, Irvine, where he focused his research on information flow tracking techniques within web browsers. Prior to being a graduate research scholar, he received a M.Sc. and B.Sc. in Computer Science from the Technical University Graz, Austria.
2025-06-11
Research Visit
Lecture by Pierluigi Nuzzo (UC Berkeley) “Assume-Guarantee Contracts for Trustworthy Autonomous Cyber-Physical Systems“
Location: TU Wien, EI 2 Pichelmayer HS (Gußhausstraße 25-25a, 1040 Wien) (CF0235
)
Time: 17:00 ‒ 19:00
Abstract: Increasingly more sophisticated tasks that were previously allocated to humans are expected to be performed by software, including modern artificial intelligence (AI) methods, in a variety of mission-critical cyber-physical systems, for example, in avionics, automobiles, robotics, and manufacturing. One of the biggest challenges to trustworthy autonomy is arguably in showing that these software and AI-enabled autonomous functions, running on heterogeneous, interconnected sensing, computation, and actuation platforms, will still satisfy the stringent safety and dependability requirements of mission-critical systems in uncertain or unpredictable environments. In this talk, I will introduce our approach to design-time assurance for autonomous cyber-physical systems, leveraging the rich modeling and specification formalism of assume-guarantee contracts and their probabilistic extensions. I will present how contracts enable compositional, quantitative requirement analysis and system verification in the presence of uncertainty as well as correct-by-construction, logically constrained decision-making and learning under uncertainty. I will then discuss how contracts can provide the semantic foundation for the automated construction of assurance cases, structured arguments about system dependability, which can accelerate system certification and help transition from a process-driven to a property-driven and evidence-based certification approach. Finally, I’ll conclude with a vision, mediated by contracts, for continuous assurance of intelligent autonomous systems.
Bio: Pierluigi Nuzzo is an Associate Professor in the Department of Electrical Engineering and Computer Sciences at UC Berkeley. Before joining UC Berkeley, he was the Kenneth C. Dahlberg Chair and an Associate Professor of Electrical and Computer Engineering and Computer Science at the University of Southern California. He received a PhD degree from UC Berkeley, and BS and MS degrees from the University of Pisa and the Sant’Anna School of Advanced Studies in Pisa. He also held research positions at the University of Pisa and IMEC, Leuven, Belgium, working on mixed-signal integrated circuit design. His research revolves around high-assurance design of cyber-physical systems and systems-on-chip, spanning the whole spectrum from the mathematical foundations to design tools and applications, with emphasis on compositional methods for system design and requirement engineering. His research interests include methodologies and tools for the design, verification, and certification of artificial intelligence and autonomous systems, and the analysis and design of secure and trustworthy hardware platforms. His awards include the IEEE Council on Electronic Design Automation (CEDA) Ernest S. Kuh Early Career Award, the Okawa Research Grant, the IEEE Technical Committee on Cyber-Physical Systems Early-Career Award, the DARPA Young Faculty Award, the NSF CAREER Award, the UC Berkeley EECS David J. Sakrison Memorial Prize, and several best paper and design competition awards.
2025-06-10
Research Visit
Lecture by Bart Mennink (Radboud University Nijmegen) “Security of the Ascon Modes“
Location: TU Graz, ISEC seminar room (IFEG042), Inffeldgasse 16a
Time: 9:30 ‒ 10:30
Abstract. The Ascon authenticated encryption scheme and hash function of Dobraunig et al. (Journal of Cryptology 2021) were recently selected as winner of the NIST lightweight cryptography competition. The mode underlying Ascon authenticated encryption (Ascon-AE) resembles ideas of SpongeWrap, but not quite, and various works have investigated the generic security of Ascon-AE, all covering different attack scenarios and with different bounds. This work systematizes knowledge on the mode security of Ascon-AE, and fills gaps where needed. We consider six mainstream security models, all in the multi-user setting: (i) nonce-respecting security, reflecting on the existing bounds of Chakraborty et al. (ASIACRYPT 2023, ACISP 2024) and Lefevre and Mennink (SAC 2024), (ii) nonce-misuse resistance, observing a non-fixable flaw in the proof of Chakraborty et al. (ACISP 2024), (iii) nonce-misuse resilience, delivering missing security analysis, (iv) leakage resilience, delivering a new security analysis that supersedes the informal proof sketch (though in a different model) of Guo et al. (ToSC 2020), (v) state-recovery security, expanding on the analysis of Lefevre and Mennink, and (vi) release of unverified plaintext, also delivering missing security analysis. We also match all bounds with tight attacks (up to constant and up to reasonable assumptions). As a bonus, we systematize the knowledge on Ascon-Hash and Ascon-PRF.
Bio: Bart Mennink received his PhD in May 2013 from KU Leuven, Belgium, and has subsequently been a postdoctoral researcher at KU Leuven and in the Digital Security group at Radboud University Nijmegen. Currently, he is associate professor on cryptography in the Digital Security Group at Radboud University Nijmegen. His main field of research is the design and provable security of symmetric cryptographic protocols, with the current focus on lightweight authentication and encryption. Bart Mennink is co-designer of Chaskey, and ISO standardized MAC function, and of COLM, an authenticated encryption scheme that was selected for the final portfolio of the CAESAR competition. He is furthermore co-designer of Elephant and ISAP, finalist authenticated encryption schemes in the NIST Lightweight Cryptography competition. Bart has published over 100 articles, he has been (co-)organizer of multiple international conferences and workshops, and has given over 15 keynotes at various conferences and workshops.
2025-06-02 Research Visit
Stefano Trevisani and Andreas Weninger from TU Wien recently visited the Institute of Information Security at TU Graz, where they gave engaging talks on their research. Their presentations sparked lively and open discussions about strengthening security in today’s increasingly complex computing environments. In addition to the talks, Stefano and Andreas met with researchers from TU Graz in a series of productive and informal meetings, where they exchanged ideas, shared insights on ongoing projects, and explored possibilities for future collaboration. These conversations set the stage for joint research projects, student exchanges, and co-authored publications between the research groups at TU Wien and TU Graz.
Polycrypt: Beyond the Linicrypt model
Abstract: The Linicrypt framework (Carmer and Rosulek, Crypto’16) provides a foundation for systematic, automated reasoning about cryptographic programs whose primitive instructions include randomly sampling, evaluating linear combinations, and querying a random oracle over some known finite field. Later, McQuoid et al. (TCC’19) gave a characterization of collision and second-preimage resistance for a class of programs, for which such properties can be checked in polynomial time. Other works have then extended similar characterizations to alternative notions either in the pseudo-random permutation (PRP) or in the ideal cipher (IC) model. None of these variations provides a way to reason about programs which employ non-linear operations over their state.
In this talk we will introduce the Polycrypt framework, an extension of Linicrypt which admits the evaluation of arbitrary polynomial transformations over the underlying field. We show how to algebraically represent such programs, and in particular we demonstrate how it naturally allows us to model important security properties such as collision and second preimage resistance. We characterize a class of “sparse” programs which admits a polynomial-time algorithm to establish collision/second-preimage resistance. We also show that Polycrypt can be readily extended to the IC model, where it can be employed to automatically verify security properties of constructions that intrinsically make use of non-linear components, such as the Galois Counter Mode (GCM) and extensions thereof.
Tweakable Enciphering Modes and their Committing Security
Abstract: A tweakable enciphering mode (TEM) is a cryptographic primitive that provides length-preserving encryption. In 2024, the National Institute of Standards and Technology (NIST) issued the Accordion call to standardize future-proof TEMs. TEMs serve as building blocks for various modes of operation, including authenticated encryption (AE), deterministic AE (DAE) and disk encryption. NIST has identified context commitment (CMT-4) as an important security objective for TEMs when used in AE/DAE.
We will start the talk by discussing the challenges of CMT-4 secure TEMs. In particular, we show that many existing TEMs, such as HCTR2 and Adiantum, fail to achieve CMT-4. We discuss different approaches to remedy the situation, and conclude our talk by proposing novel TEM designs, which are the first to achieve provably CMT-4 security.
2025-06-02
Defense
Sophie Rain (TU Wien) successfully defended her PhD thesis titled “Automated Security Analysis of Blockchain Protocols”
Her doctoral research was supervised by Univ.-Prof.in Dr.in techn. Laura Kovacs (TU Wien). The thesis was reviewed by two esteemed experts in the field: Prof. Ruzica Piskac (Yale University) and Prof. Vincent Cheval (University of Oxford). Sophie Rain`s dissertation advances blockchain security by addressing both the design and implementation levels of protocols. On the theoretical side, she develops a novel framework for game-theoretic security analysis, using extensive form games, symbolic payoffs, and automated reasoning. This includes a formal definition of game-theoretic security and the development of CheckMate, a tool that enables scalable, automated analysis of protocol incentives. On the implementation side, she introduces a generalization of Presburger arithmetic to formally verify properties involving unbounded summations in smart contracts. This strengthens the verification of blockchain protocol implementations and improves their practical security. Together, these contributions offer a comprehensive and automated approach to ensuring both incentive correctness and implementation soundness in blockchain systems.
2025-06-02
Research Visit
Lecture by Erwin Quiring (Ruhr-University Bochum) “On the Misuse Of Generative AI and What We Can Do About It“
Location: TU Wien, FAV Hörsaal 3 Zemanek (Seminarraum Zemanek, Favoritenstraße 9-11, Erdgeschoß) (HEEG02
)
Virtual location: https://live.video.tuwien.ac.at/watch?l=wUSYcGK83g1TCxLqRtEuF
Time: 17:00 ‒ 18:00
Abstract: The emergence of generative artificial intelligence (AI) has revolutionized content creation, enabling us to produce highly authentic digital media such as images, videos, texts, and music that is hard to distinguish from real media. Despite many positive applications, this also leads to considerable concerns on the misuse potential, such as recent incidents in elections or recent phishing attempts have effectively demonstrated. In my talk, we revisit how AI is misused and how it might be misused in the future. Then, we dive into possible countermeasures to mitigate this misuse, including passive detection approaches and recent watermarking trends.
Bio: Erwin Quiring is a researcher at the Ruhr University Bochum, Germany. He received a Ph.D. in computer science from TU Braunschweig and has worked as postdoctoral researcher at ICSI @ UC Berkeley from 2023 to 2024. His research vision is to foster the trustworthiness of AI. In particular, he works on the reliability, efficiency, and security of AI. One of this main research areas is the detection of AI-generated content. Contact him at erwin.quiring@rub.de
May 2025
2025-05-30
Research Visit
Lecture by Ghassan Karame (Ruhr-University Bochum) “Larger Decentralized Platforms Don`t Necessarily Offer Better Security“
Location: TU Wien, FAV Hörsaal 1 Helmut Veith - INF (Favoritenstraße 9-11, Erdgeschoß) (HEEG02
)
Virtual location: https://live.video.tuwien.ac.at/watch?l=beJAN1gHpvaihUhG2habKP
Time: 10:00 ‒ 11:00
Abstract: Decentralized platforms support transparency and enable open access and participation. It is expected that decentralization will stimulate innovation and will positively impact the digital experience of many enterprises around the globe, e.g., in applications for payments, machine learning, social networks, etc. Unfortunately, the precise relationship between “decentralization” and platform security remains unclear. It is commonly believed that greater decentralization improves security by distributing power across more nodes. Yet, in some applications, an increasing number of nodes also leads to higher network delays, and the extent to which these delays impact security is not well understood. In this talk, I will explore how decentralization influences the security of two prominent emerging decentralized applications: Nakamoto-style blockchains and Decentralized Machine Learning.
Bio: Since November 2021, Ghassan Karame is a full Professor of Computer Science at the Ruhr-University Bochum (RUB) - leading the Chair for Information Security. Ghassan is a Principal Investigator (PI) in the Cluster of Excellence CASA (Cyber Security in the Age of Large-Scale Adversaries) and, since October 2023, the Director (and a PI) at the Horst Goertz Institute for IT Security (HGI). He is also involved as a (part-time) Chief Scientific Advisor at NEC Laboratories Europe. Before joining RUB, he was working as an NEC Fellow and was leading the Security research group at NEC Labs in Germany. Prior to joining NEC Labs, he was working as a postdoctoral researcher in the Institute of Information Security of ETH Zurich, Switzerland. Since 2011, he holds a PhD degree in Computer Science from ETH Zurich. Ghassan is interested in all aspects of security and privacy with a focus on decentralized security, and platform security.
2025-05-27
Outreach to society
Martina Lindorfer and Matteo Maffei will join the panel ‘Cybersecurity in New Times’ at the Digital Humanism Conference.
The first Digital Humanism Conference will take place from May 26 to 28, 2025, in Vienna, focusing on the theme “Shaping our digital future.” The event will gather global thinkers, innovators, and policymakers to discuss the potential of Digital Humanism and its impact on society.
2025-05-20
Invited Talk
Arnab Roy (University of Innsbruck) gave a talk on Lightweight Symmetric Cryptography
2025-05-15
Outreach to society
Maria Eichlseder is a speaker at the NCC-AT Community Event 2025
The NCC-AT Community Event 2025 focuses on advancing innovation in cybersecurity by bridging the gap between research and practical application. The event aims to foster synergies, accelerate innovation, and promote knowledge transfer across academia, industry, and the public sector. Keynotes will address current cybersecurity strategies, best practices from research and implementation, funding opportunities, and offer networking with experts from across the Austrian cybersecurity ecosystem.
2025-05-14
Outreach to society
Roderick Bloem took part in a panel discussion at the symposium “Computer Science in Education: By Humans, for Humans“
The symposium Computer Science in Education: By Humans, for Humans , organized by the Austrian Computer Society (OCG) in cooperation with CEPIS, brought together academic and industry experts to discuss the future of computing education across three key areas, including the role of computer science in promoting digital empowerment. During the panel titled “The Austrian View – Computer Science and its Contribution to Empowered Citizens,” Prof. Bloem emphasized the increasing importance of computer science in a rapidly evolving world and advocated for recognizing informatics as a core subject, on par with other school curriculum disciplines. He stressed that computing education should extend beyond programming to foster critical thinking and build self-confidence.
2025-05-07
Research Visit
Lecture by Johannes Buchmann (Center for Advanced Security Research Darmstadt) “Sustainable Cybersecurity“
Location: TU Wien , Campus Karlsplatz, Hörsaal 7 Schütte-Lihotzky (1040 Vienna, Karlsplatz 13, Erdgeschoss) (AHEG07
)
Time: 15:00 ‒ 17:00
Abstract: Information technology plays a crucial role in all areas of society, the economy, and science. Therefore cybersecurity is of utmost importance. But it is not enough to ask whether security is guaranteed at present. Instead, we must also consider whether cybersecurity is ensured in a sustainable manner—for example, whether protection mechanisms remain effective over the long term. In this talk, we outline the key protection goals that cybersecurity technologies must achieve. We discuss what sustainability means in the context of these goals and examine the extent to which current technologies can meet these requirements. Finally, we explore the scientific challenges that need to be addressed in order to ensure sustainable cybersecurity and privacy in the future.
Bio: Johannes Buchmann is a computer scientist and mathematician. He developed algorithmic algebraic number theory for cryptographic applications, and gained worldwide recognition through his research in the field of cryptography. Johannes Buchmann developed cryptographic methods, such as encryption and electronic signatures, and his work also focuses on issues of data protection and privacy. Johannes Buchmann attaches great importance to the development of crypto procedures that can also withstand attacks by quantum computers (post-quantum crypto procedures). Researchers assume that there will be quantum computers in the future that can override many of today’s cryptological security procedures (RSA, ECC). In their work, Johannes Buchmann and his team are addressing issues of long-term security – in particular the long-term storage of confidential data, and the long-term archiving of signed documents. Johannes Buschmann co-founded the Center for Advanced Security Research Darmstadt and FlexSecure GmbH in in cooperation with the company T-Systems and the German Center for Artificial Intelligence (DZKI).
2025-05-05
Research Visit
Attacking and Securing Leaky Systems at the Hardware-Software Boundary
Jonas Juffinger (TU Graz) recently visited the University of Vienna to deliver an insightful talk on vulnerabilities and security challenges at the intersection of hardware and software systems. The talk sparked engaging discussions among attendees, highlighting the importance of strengthening security measures in increasingly complex computing environments. This visit also fostered collaboration opportunities between TU Graz and the University of Vienna, contributing to advancing research in hardware-software security.
April 2025
2025-04-25
Outreach to society
Matteo Maffei joined the discussion “Artificial Intelligence in Research and Innovation” at ASSAI event.
The Association for Scientific Exchanges between Austria and Italy (ASSAI) brings together Italian academics and researchers residing and working in Austria. The first session of “In Dialogo con ASSAI” kicked off a promising series of events centered on “Artificial Intelligence in Research and Innovation.” This event gathered experts from various fields, including physics, cybersecurity, linguistics, and sociology, to delve into the practical impacts of AI. Prof. Matteo Maffei shared deep insights on how AI is being integrated into cybersecurity. The discussions explored how these technological advancements are shaping current and future security protocols, demonstrating the vast applications and implications of artificial intelligence.
2025-04-22
Research Visit
Lecture by Ruzica Piskac (Yale University) “Realizing Leibniz`s Dream - Automating Legal Reasoning”
Location: TU Graz, ISEC seminar room (IFEG042), Inffeldgasse 16a
Time: 9:00 - 10:00
Abstract: In the 17th Century, the philosopher, mathematician and lawyer Gottlieb Leibniz envisioned the creation of a characteristica universalis and calculus ratiocinator that would enable reasoning in law and morals as systematically as in geometry and analysis. His goal was to resolve legal disputes with the precision and clarity with which accountants settle financial discrepancies. We are now, for the first time in history, positioned to realize Leibniz’s dream of automating legal reasoning. The crucial step in this process is the alignment of sophisticated computer science techniques with appropriate types of legal problems. Automating code-based legal reasoning, which relies on explicit statutes and regulations, differs fundamentally from automating case-based reasoning, which depends on precedents and interpretations. We will discuss how formal methods and Large Language Models (LLMs) can be utilized to achieve what Leibniz envisioned three centuries ago, effectively transforming the landscape of legal reasoning through the power of modern computational technology.
Bio: Ruzica Piskac is a Professor of Computer Science at Yale University, where she leads the Rigorous Software Engineering (ROSE) group. Her research interests span the areas of software verification, security and applied cryptography, automated reasoning, and code synthesis. Much of her research has focused on using formal techniques to improve software reliability and trustworthiness. Piskac joined Yale’s Department of Computer Science in 2013.
She was previously an Independent Research Group Leader at the Max Planck Institute for Software Systems in Germany. Her research has received a range of professional honors, including multiple Amazon Research Awards, Yale University’s Ackerman Award for Teaching and Mentoring, the Facebook Communications and Networking Award, and the Microsoft Research Award for the Software Engineering Innovation Foundation (SEIF). In 2019, Yale named Piskac the Donna L. Dubinsky Associate Professor of Computer Science.
Piskac holds a Ph.D. from the Swiss Federal Institute of Technology (EPFL), where her dissertation won the Patrick Denantes Prize. Her current and recent professional activities include service as Program Chair of the 37th International Conference on Computer Aided Verification and the Steering Committee of the Formal Methods in Computer-Aided Design conference. Piskac has graduated five PhD students, four of them are currently holding a position of an assistant professor of computer science.
2025-04-19
Presentation
SPyCoDe Members Present Four Cutting-Edge Papers at Financial Cryptography and Data Security 2025
At the 29th International Conference on Financial Cryptography and Data Security (FC 2025 ), four innovative research papers created with the participation of SPyCoDe members were presented. These works address critical challenges in blockchain technology, secure payments, and cryptographic protocols, pushing the boundaries of efficiency, scalability, and security.
X-Transfer: Enabling and Optimizing Cross-PCN Transactions
Authors: Lukas Aumayr, Zeta Avarikioti, Iosif Salem, Stefan Schmid, Michelle Yeo
Blockchain interoperability allows assets to move between different chains, but cross-chain transactions on Layer‑2 payment channel networks (PCNs) have remained a challenge due to reliance on on‑chain events. X-Transfer introduces the first fully off‑chain, secure, and scalable protocol for payments across multiple PCNs. Using transaction aggregation, it boosts liquidity and throughput while reducing fees. Empirical results show it can achieve more than double the throughput of current approaches, marking a major step forward in multi‑chain financial operations.
On the (In)Security of Proofs-of-Space Based Longest-Chain Blockchains
Authors: Krzysztof Pietrzak, Mirza Ahad Baig
Proofs of space (PoSpace) have been proposed as an eco‑friendly alternative to proof of work in blockchain consensus. However, this work shows that without extra assumptions, PoSpace‑based longest‑chain protocols cannot be secure under dynamic resource availability. The authors rigorously quantify the limits of such protocols and demonstrate the need for additional cryptographic primitives, such as verifiable delay functions. The findings have direct implications for the design of future sustainable blockchain systems, including networks like Chia.
Blink: An Optimal Proof of Proof‑of‑Work
Athors: Lukas Aumayr, Zeta Avarikioti, Matteo Maffei, Giulia Scaffino, Dionysis Zindros
Light clients are crucial for enabling secure, resource‑efficient blockchain interactions, especially in cross‑chain applications. Existing solutions either require significant resources or rely on trusted setups. Blink is the first provably secure, interactive proof‑of‑work light client with O(1) complexity that does not require a trusted setup. It reduces Bitcoin state verification from tens of megabytes to just 1.6 KB, making it a powerful tool for payment verification, blockchain bootstrapping, and decentralized bridges.
Anthemius: Efficient & Modular Block Assembly for Concurrent Execution
Authors: Ray Neiheiser, Lefteris Kokoris-Kogias
Many blockchains process transactions sequentially, creating a major throughput bottleneck. While parallel execution engines exist, their benefits are often limited when transactions conflict over shared resources. Anthemius tackles this by introducing a novel block construction algorithm that optimizes for parallel execution. It enables blockchains to process more than twice as many transactions under realistic workloads, unlocking the full potential of multi‑core architectures for blockchain scalability.
Watch the full presentation on YouTube
2025-04-03
Research Visit
Lecture by Grigory Fedyukovich (Florida State University) “Maximizing Branch Coverage with Constrained Horn Clauses
Location: TU Wien , EI 4 Reithoffer HS (Haupttrakt, Gußhausstraße 25-25a, 2. Stock) (CF0245
)
Time: 15:00 ‒ 16:00
Abstract: State-of-the-art solvers for constrained Horn clauses (CHC) are successfully used to generate reachability facts for software using its symbolic encoding. In this talk, I will present a new application of CHCs to test-case generation, a problem of finding a set of tuples of input values to a program under which the program visits as many branches as possible. The key insight to achieve maximality is to identify and skip blocks of code that are provably unreachable. The new approach to test case generation called HORNTINUUM uses CHC to construct different program unrollings incrementally and extract test cases from models of satisfiable formulas. At the same time, a CHC solver keeps track of CHCs that represent unreachable blocks of code, making the unrolling process more efficient. In practice, this lets HORNTINUUM terminate early while guaranteeing maximal coverage. HORNTINUUM exhibits promising performance: it generates high coverage in most cases and takes less time on average than state-of-the-art based on bounded model checking, concolic execution, and/or fuzzing.
Bio: Grigory Fedyukovich is an Assistant Professor at Florida State University. He completed his Ph.D. at the University of Lugano under the supervision of Prof Natasha Sharygina, a postdoc at the University of Washington with Prof Rastislav Bodik, and a postdoc at Princeton University with Prof Aarti Gupta. His main research interests are in the fields of automated reasoning, software verification, and synthesis.
March 2025
2025-03-17
Award
Barbara Gigerl received her doctorate sub auspiciis, a recognition for exceptional academic achievements, under the auspices of the Federal President of the Republic of Austria
Barbara Gigerl from TU Graz received her doctorate under the auspices of the President of the Republic (Promotio sub auspiciis Praesidentis rei publicae) in recognition of her exceptional achievements in both school and university. The graduation ceremony
, performed by Peter Riedler, Rector of the University of Graz, and Horst Bischof, Rector of Graz University of Technology (TU Graz), took place on Friday, 14 March 2025, in the Great Hall of the Old University of Graz. Subsequently, Federal President Alexander Van der Bellen personally presented the Ring of Honour featuring the Federal Eagle of the Republic of Austria to the graduates at a reception in the Vienna Hofburg on 17 March 2025. This event
celebrates her outstanding academic accomplishments.
Thesis
2025-03-10
Research Seminar
SnailLoad: Exploiting Remote Network Latency Measurements without JavaScript
2025-03-10
Public Lecture
Maria Eichlseder delivered a lecture at the Cluster of Excellence CASA
Maria Eichlseder presented Automated Tools for Symmetric-Key Cryptanalysis at the Spring School on Symmetric Cryptography .
2025-03-06
Outreach to society
Austria’s largest education fair BeSt
Martina Lindorfer joined the TU Wien team at BeSt, the prominent education fair, where they showcased the university’s diverse degree programs. Alongside other team members, she represented ongoing research in security and privacy at TU Wien. She engaged with attendees, answering questions and providing a hands-on look at what studying Computer Engineering at TU Wien involves.
2025-03-04
Research Visit
Lecture by Jonathan Katz (Google) “Round-Optimal Fully Secure Distributed Key Generation“
Location: TU Wien, TU Wien, FAV Hörsaal 1 Helmut Veith (Favoritenstraße 9-11, Erdgeschoß)
Time: 15:00 ‒ 16:00
Abstract: Protocols for distributed (threshold) key generation (DKG) in the discrete-logarithm setting have received a tremendous amount of attention in the past few years. Several synchronous DKG protocols have been proposed, but most such protocols are not fully secure: they either allow corrupted parties to bias the key, or are not robust and allow malicious parties to prevent successful generation of a key.
We explore the round complexity of fully secure DKG in the honest-majority setting where it is feasible. We show the impossibility of one-round, unbiased DKG protocols (even satisfying weaker notions of security), regardless of any prior setup. On the positive side, we show various round-optimal protocols for fully secure DKG offering tradeoffs in terms of their efficiency, necessary setup, and required assumptions.
Video
Paper
Bio: Jonathan Katz recently joined Google as a Senior Staff Research Scientist, after more than 20 years as a professor at the University of Maryland where he also served as director of the Maryland Cybersecurity Center. He is a co-author of the widely used textbook “Introduction to Modern Cryptography” (now in its third edition) and also offers a free online course on cryptography through Coursera. Katz has received an Alexander von Humboldt Research Award, a UMD Distinguished Scholar-Teacher Award, and an ACM SIGSAC Outstanding Contribution Award. He is a fellow of the IACR and the ACM.
February 2025
2025-02-28
Outreach to society. Female Mentoring Session
Radical Software: Women, Art & Computing 1960–1991
SPyCoDe supports the symposium organized by TU Wien Informatics, Kunsthalle Wien, and the Wolfgang Pauli Institute (WPI), which is part of an exhibition
examining the history of digital art through a feminist lens. The focus is on women who used computers as both tools and subjects, and on artists whose work is inherently computational. Co-organizer Prof. Laura Kovács views the symposium as an essential platform for discussing the central themes of the exhibition, which showcases contributions from distinguished female researchers and artists. Keynote speeches and panel discussions will underscore and delve into the pivotal roles women have played in advancing computer technology and digital art. Additionally, within the Q&As, panel discussions and closing networking events, female participants will have further opportunities to interact and discuss with prominent role models in computer science, in particular with Ina Wagner
(TU Wien), Nadia Thalmann
(MIRALab, University of Geneva), and Gerti Kappel
(TU Wien Informatics).
The full program is available here
.
2025-02-26
Presentation
NDSS Symposium 2025
The Network and Distributed System Security Symposium (NDSS
) 2025, which took place in San Diego, California from February 24 to 28, showcased four impactful papers from SPyCoDe researchers. These works explored advanced topics ranging from blockchain security to innovative attack vectors.
One notable presentation, “Alba: The Dawn of Scalable Bridges for Blockchains
” by G. Scaffino, L. Aumayr, M. Bastankhah, Z. Avarikioti, and M. Maffei, introduced the Pay2Chain bridge. This innovative tool leverages off-chain solutions to enhance the efficiency of blockchain interoperability, demonstrating secure, efficient, and trustless transactions based on off-chain events.
Another critical study, “CounterSEVeillance: Performance-Counter Attacks on AMD SEV-SNP
” by S. Gast, H. Weissteiner, R.L. Schröder, and D. Gruss, revealed a novel side-channel attack that exploits performance counter data in AMD’s confidential virtual machines. This research demonstrates how sensitive data can be extracted, posing significant implications for the security of virtual environments.
Additionally, “KernelSnitch: Side-Channel Attacks on Kernel Data Structures
” by L. Maar, J. Juffinger, T. Steinbauer, D. Gruss, and S. Mangard, detailed a method for exploiting kernel data structures to extract sensitive information. This attack illustrates vulnerabilities in systems, even those without shared hardware elements.
Lastly, “Secret Spilling Drive: Leaking User Behavior through SSD Contention
” by J. Juffinger, F. Rauscher, G. La Manna, and D. Gruss, investigated how SSD contention could be used to create a covert channel that leaks user behavior. This study highlights the security risks associated with modern SSDs and their implications for user privacy.
These papers not only address current security challenges but also propose innovative solutions, demonstrating SPyCoDe’s significant contributions to the field of network and system security.
2025-02-24
Presentation
Florian Holzbauer delivered a talk at the AT:NOG event
Florian Holzbauer presented at the AT:NOG event on active measurement techniques for detecting internet outages, focusing on connectivity monitoring between Austria and Ukraine. His talk highlighted the CountryMonitor system, which performs frequent scans to identify network disruptions caused by infrastructure damage, conflicts, or other factors. Case studies from Ukraine demonstrated how outages affect network reliability and emphasized the importance of proactive monitoring to improve network resilience and support crisis management.
2025-02-20
Keynote
Daniel Gruss delivered the keynote ‘Every Threat Model is Wrong’ at RuhrSec 2025.
Abstract. Security is the tension between an adversary trying to break into a system and a defender trying to prevent this. This game is inherently asymmetric, as the defender tries to anticipate what the adversary could do and the adversary tries to find anything the defender overlooked. Thus, it is at the core of security that threat models are time and again invalidated. In this keynote, we’ll explore some historic examples including the change from isolated to interconnected systems, the change of the root of trust with TEEs, and lastly the change from carbon-ignorant security to carbon-aware security. Finally, we will discuss why threat models are still relevant and how they can guide security research in a constantly evolving landscape.
2025-02-19
Presentation
Jonas Juffinger presented at the 1st Microarchitecture Security Conference (uASC ‘25).
Title. An Analysis of HMB-based SSD Rowhammer
Abstract. Rowhammer has been shown to be an extensive attack vector. In the years since its discovery, numerous exploits have been shown, attacking a wide range of targets from kernels, through web browsers to machine learning models. These attacks were not always mounted from code running on the CPU of a system. Various devices peripheral to the CPU, like GPUs or network cards, can cause Rowhammer bit flips through DMA accesses to the main memory.
In this work, we take a look at solid state drives (SSDs) and if they can be exploited as confused deputies to perform Rowhammer attacks. With the introduction of NVMe, a standardized protocol that allows SSDs to communicate directly over PCIe with the CPU, SSDs have reached performance numbers of a million input/output operations per second. PCIe also enables SSDs to use DMA for direct accesses to the main memory. This led to the introduction of the host memory buffer (HMB) feature, that allows SSDs to use a small fraction of the host DRAM. We are the first to reverse engineer how different SSDs utilize this host memory buffer and answer the question if the accesses from the SSD to the HMB are a potential attack vector to cause Rowhammer bit flips.
Our analysis of three SSDs shows that bit flips in the HMB cause the SSDs to lock up, which results in a denial of service or, even worse, data loss. We also show how we can cause frequent accesses from the SSD to the HMB on all three SSDs. On one SSD, we reach 5,000 DRAM accesses per refresh interval. We measure the Rowhammer impact of these accesses and show that they are effectively hammering the DRAM. However, 5,000 DRAM accesses are not enough to cause Rowhammer bit flips, even on modern, highly vulnerable DRAM.
January 2025
2025-01-31
Outreach to society
Computer science is general education and should become a mandatory subject.
In his guest commentary for Der Standard, Prof. Roderick Bloem argues that computer science should become a mandatory subject in Austrian schools, on par with mathematics and German. He emphasizes that in the digital age, understanding core concepts of computer science—such as algorithmic thinking, abstraction, programming, and problem analysis—is essential for all citizens to navigate the modern world critically and responsibly.
Bloem highlights the limitations of current digital education, which primarily focuses on media literacy and the ethical use of technology. He argues that this should be complemented by computer science as a distinct subject. He outlines several key benefits of making computer science a mandatory subject. First, it ensures that digital literacy becomes an essential part of general education. It also improves students’ career prospects and helps address the shortage of skilled professionals. By introducing children — especially girls — to future-oriented topics, it promotes greater diversity in the field. Furthermore, it empowers society to shape digital policy independently and responsibly. Finally, computer science is engaging and directly relevant to everyday life.
Bloem also points to the lack of qualified computer science teachers in Austria and calls for action. He suggests that establishing computer science as a full subject with final exams (Matura) would motivate more students to pursue teaching degrees in informatics.
He concludes by urging the next Austrian government to take immediate steps to establish Austria as a leader in digital education.
2025-01-29
Outreach to society
Vienna Innovation Conference
Martina Lindorfer participated in the panel ‘@Risk: Are Our Data Safe?’ at the 10th Vienna Innovation Conference. The discussion explored the evolution of data security, the impact of artificial intelligence, and Vienna’s standing in the global cybersecurity landscape.
2025-01-28
Presentation
Stefano Trevisani presented at the “Algebraic Aspects in the Design and Cryptanalysis of Modern Symmetric Cryptography” workshop (ALPSY)
The presentation, ‘Flexible Modes for Arithmetization-Oriented Compression Functions: Verifiable Computation and ZK-SNARKs,’ explored the intricate relationship between hash functions and ZK-SNARKs, specifically focusing on arithmetization-oriented hash functions and compositional paradigms. It introduced two innovative families of modes, PGV-ELC and ELC-P, aimed at enhancing the flexibility and security of cryptographic systems. Stefano emphasized the security features of these modes, especially their indifferentiability, which is vital for the robustness of cryptographic schemes. He also provided a comprehensive comparison of the security aspects of these modes, supported by benchmarking results from Groth16 and Plonky2 to assess their real-world performance. Furthermore, discussions on Merkle Tree arity benchmarks illustrated the efficiency of these modes across different configurations, aligning them with strategic cryptographic design objectives.
2025-01-27
Public Lecture
Georg Fuchsbauer will give a talk on “Space-efficient blockchains“
The talk is a part of the Public Lecture Series ‘Sustainability in Computer Science’ under the auspices of Informatik Austria .
Abstract. The move from “proof of work” to “proof of stake” has arguably overcome the problem of energy waste in blockchains. However, for public verifiability, most systems require all transactions to be stored forever, by every full node. In Bitcoin this data now amounts to over 600GB, while in Ethereum it is over 1TB. We will overview two approaches to space-efficient systems. “Mimblewimble” is a protocol where spent transactions can be erased from the blockchain while maintaining verifiability. “Mina” goes further and, using a heavy-weight cryptographic concept called zk-SNARK, reduces its blockchain size to 22kB, which will never grow.
December 2024
2024-12-20
Research Visit
Lecture by Christoph Kerschbaumer (Mozilla) “Towards a Secure and Privacy-Respecting Web“
Location: TU Wien, FAV Hörsaal 1 Helmut Veith (Favoritenstraße 9-11, Erdgeschoß) (HEEG02
)
Time: 11:00 ‒ 12:00
Abstract. The Hypertext Transfer Protocol, generally displayed as http in a browsers address-bar, is the fundamental protocol through which web browsers and websites communicate. However, data transferred by the regular http protocol is unprotected and transferred in cleartext, such that attackers are able to view, steal, or even tamper with the transmitted data. Carrying http over the Transport Layer Security (TLS) protocol, generally displayed as https in the address-bar of a browser, fixes this security shortcoming by creating a secure and encrypted connection between the browser and the website.
Bio: Dr. Christoph Kerschbaumer has over two decades of experience in software engineering and computer security. His work ranges from designing secure systems with fail-safe defaults to fighting cross-site scripting to preventing man-in-the-middle attacks. Currently he is managing the Firefox Security Engineering team at Mozilla and is mentoring software engineers around the world to reach their full potential. He received his PhD in Computer Science from the University of California, Irvine, where he focused his research on information flow tracking techniques within web browsers. Prior to being a graduate research scholar, he received a M.Sc. and B.Sc. in Computer Science from the Technical University Graz, Austria.
2024-12-19
Outreach to society
KURIER-TV’s “Spontan gefragt”
Martina Lindorfer joined the recent episode of KURIER-TV’s “Spontan gefragt” as an IT security expert and computer scientist. Along with IT and business consultant Georg Krause, she discussed the complex world of cybercrime, shedding light on the sophisticated nature of modern hacking operations and explored various aspects of digital threats and defensive strategies.
2024-12-09
Recognition
Martina Lindorfer is named a Senior Fellow at the Applied Computer Security Associates (ACSA)
The prestigious recognition follows Martina’s outstanding contributions, including two years as Program Committee Chair at Annual Computer Security Applications Conference and two prior years as Artifact Evaluation Chair.
November 2024
2024-11-26
Research Visit
Lecture by Adam O’Neill (University of Massachusetts, Amherst) “Idealized Models in Cryptography: What, Why, and Where to Now?“
Location: TU Wien, TU Wien, FAV Hörsaal 2 (Favoritenstraße 9-11, Erdgeschoß)
Time: 15:00 ‒ 16:00
Abstract: Provable security is the science of building cryptographic protocols out of building blocks in a sound way. Namely, one proves the only way to break a protocol is to break one of the building blocks. But does every secure protocol have such a proof? What if we can’t find one? This talk will introduce the concept of “idealized models,” which are artificial models of computation created by cryptographers to address this issue. We will describe what idealized models are and why they are used. Then, we will describe our on-going line of research aimed at better analyses in such models, as well as ultimately transitioning the proofs to do without idealized models. This gives greater assurance in the security of many widely used cryptographic protocols. The talk will be high-level and not assume previous knowledge of cryptography.
Bio: Adam O’Neill is an Assistant Professor in the Manning College of Information and Computer Sciences at the University of Massachusetts, Amherst. Previously, he was an Assistant Professor of Computer Science at Georgetown University. He received his Ph.D. in Computer Science at the Georgia Institute of Technology and held postdoctoral appointments at the University of Texas at Austin and Boston University. Recently, he received the CRYPTO 2022 Test-of-Time Award.
2024-11-25
Public Lecture
Krzysztof Pietrzak will give a talk on “Sustainable Blockchains“
The talk is a part of the Public Lecture Series ‘Sustainability in Computer Science’ under the auspices of Informatik Austria .
Abstract. The Bitcoin blockchain achieves consensus in an open setting, i.e., where everyone can participate. This was believed to be impossible, the key idea to make this possible was to use computing power rather than some kind of identities for voting through “proofs of work”. Unfortunately, this approach is not sustainable: the Bitcoin blockchain burns roughly as much electricity as a country like Austria. We will outline sustainable alternatives for achieving a Bitcoin-like blockchain, with a focus on using disk space instead of computation and how this is realized in the Chia Network blockchain.
2024-11-24
Outreach to society
Johanna Ullrich contributed to the panel discussion on AI & Security
The discussion was part of the event “AI and Security – A multidisciplinary approach” organized by the Department of Innovation and Digitalisation in Law of University Vienna. Video
2024-11-18
Outreach to society
FinTechWeek Vienna Opening 2024: Cybersecurity in the Age of AI
Prof. Matteo Maffei will deliver a keynote at FinTechWeek Vienna Opening 2024. As artificial intelligence continues to transform the cybersecurity landscape, it introduces both new risks and opportunities. The keynote will explore the extensive impacts of AI on cybersecurity, highlight key threats, and discuss collaborative research strategies to stay ahead in this dynamic field.
2024-11-15
Research Visit
Lecture by Ben Stock (CISPA Helmholtz Center for Information Security) “Reproducible and Ethical Web Security Measurements“
Location: TU Wien, TU Wien, FAV Hörsaal 2 (Favoritenstraße 9-11, Erdgeschoß)
Time: 9:00 ‒ 10:00
Abstract: The Web is a great place to measure many things: client-side headers, JavaScript functionality, or insecure server-side code. In this talk, I will share insights into Web measurements from two angles: first, can we make Web measurement reproducible by design such that others can confirm or refute our findings? Second, where are the red lines when considering server-side security checks such as looking for SQL injections?
Bio: Ben Stock is a tenured faculty at the CISPA Helmholtz Center for Information Security in Saarbrücken, Germany. Ben leads the Secure Web Application Group at CISPA, and his research focuses on various aspects of Web and network security, with a recent focus in particular on (un)usability of security mechanisms. His group regularly publishes at all major security conferences and Ben serves on the PC and in chair roles for various security conferences. Beyond the focus on academic output, together with his students, he regularly aims to bridge the gap between scientists and practitioners through talks at non-academic conferences like OWASP AppSec or Ruhrsec.
2024-11-13
Invited Talk
Lecture by Caroline Trippel (Stanford University) “Automatically Uncovering Hardware Side-Channels in Processor RTL with Multi-μPATH Synthesis“
Time: 17:00 ‒ 18:00
Location: Online
Abstract. Modern hardware side-channel defenses are designed with respect to microarchitectural leakage contracts, which characterize microarchitectures’ hardware side-channels. Numerous leakage contracts have been proposed in the literature and by industry (e.g., Arm DIT, Intel DOIT, RISC-V Zkt) to support a variety of hardware side-channel defenses, implemented in hardware or software. Yet, no automated nor scalable approach exists for formally verifying hardware adherence to any of them.
In this talk, I will present SynthLC, an automated approach/tool for synthesizing (“uncovering”) a variety of formally verified leakage contracts — which collectively support ten state-of-the-art hardware side-channel defense — from a SystemVerilog processor design, assuming an attacker that monitors program execution time or resource contention. SynthLC is built on top of another automated approach/tool, called RTL2MμPATH, for synthesizing (“uncovering”) a complete set of formally verified microarchitectural execution paths (μPATHs) for each instruction from processor RTL. This deign choice exploits our key observation: μPATH variability (>1 μPATH) for an instruction strongly indicates there is a hardware side-channel in the input design.
Bio: Caroline Trippel is an Assistant Professor in the Computer Science and Electrical Engineering Departments at Stanford University working in the area of computer architecture. A central theme of her work is leveraging formal methods techniques to design and verify hardware systems in order to ensure that they can provide correctness and security guarantees for the applications they intend to support. Trippel’s research has been recognized with and NSF CAREER Award, IEEE Top Picks distinctions, the 2024 Intel Rising Star Award, the 2023 Intel Outstanding Researcher Award, the 2020 ACM SIGARCH/IEEE CS TCCA Outstanding Dissertation Award, and the 2020 CGS/ProQuest® Distinguished Dissertation Award in Mathematics, Physical Sciences, & Engineering. She was also awarded an NVIDIA Graduate Fellowship (2017-2018) and selected to attend the 2018 MIT Rising Stars in EECS Workshop.
2024-11-08
Achievement
TUW Team Secures Third Place in CSAW Student Cybersecurity Competition
Lea Salome Brugger, a former master’s student at TU Wien and now a PhD student at ETH Zürich, won 3rd place at the CSAW Applied Research Competition in cybersecurity. She presented CheckMate , a collaborative project developed with Laura Kovács, Anja Petković Komel, Sophie Rain, and Michael Rawson. The competition was organized for the 8th time by Grenoble INP - Esisar and the LCIS laboratory, focusing on research that has a practical impact. Finalists presented their work to a jury of industrial experts.
October 2024
2024-10-28
Research Visit
Lecture by Joel Reardon (University of Calgary) “Anonymity, Consent, and Other Noble Lies: An Empirical Study of the Data Economy“
Abstract: While legal scholars have cited decades of computer science research that demonstrates why anonymity is a hard problem (and that datasets should not be labelled as “anonymous” cavalierly), industry and legal practitioners have not heeded those warnings: many organizations trafficking in consumer data continue to make assertions that, for example, hashed email addresses are anonymous and cannot reveal the original email address, and that device-based identifiers, such as advertising IDs, only identify devices and not people.
We acquired datasets from multiple data brokers to empirically demonstrate why these assertions are false. Using publicly available email addresses found in data breaches posted on the Internet, we show that one can reidentify 88% of the hashed email addresses that we obtained. Reidentifying hashed email addresses need not rely on illicit data: by constructing rainbow tables, we reidentified a majority of the hashed email addresses. In all cases, the hashed email addresses were linked to other device-based identifiers (e.g., mobile data advertising IDs, IPs, etc.), demonstrating why device-based identifiers have long been considered personally identifiable information.
Relatedly, organizations trafficking in this data make another assertion, that this data was collected from consumers with their consent. To evaluate this claim, we performed a survey (n = 369), in which we emailed the reidentified individuals in our datasets to recruit them to participate in a survey. This survey asked participants about their recollections of having provided consent and whether they would prefer that the data brokers delete their data.
Bio: Joel Reardon is an associate professor at the University of Calgary who researches mobile security and privacy issues and data collection done through those devices. He has also co-founded the privacy analytics company AppCensus. He received his Bachelors and Master’s at the University of Waterloo and his Doctor of Sciences at the ETH Zurich. His research has been covered by the CBC, the BBC, the Washington Post, and the Wall Street Journal, among other places. His research has received the Emilio Aced Research and Personal Data Protection Award, the CNIL - Inria Data Protection Award, and the Caspar Bowden Award for Outstanding Research in Privacy Enhancing Technologies. He likes bicycling and snowboarding and is currently trying to improve his French.
2024-10-23
Outreach to society
Humanistic AI in Vienna. AI and Me: The Citizens’ Perspective
Prof. Laura Kovács is a participant in the panel discussion on the impacts and benefits of AI for citizens at Vienna Digital Days 2024. The discussion will focus on the application perspective, exploring the impacts and potential benefits of AI in citizens’ daily lives. Key areas of focus will include technology assessment and security. The discussion will revolve around three primary topics: the labor market and education, data security, and health, with a particular emphasis on its effects on perception and medicine.
2024-10-21
Public Lecture
Daniel Gruss give a talk on “Sustainable Security.“
The talk is a part of the Public Lecture Series “Sustainability in Computer Science“ under the auspices of Informatik Austria . This lecture series, a pioneering initiative in Austria, unites all Austrian CS departments and faculties to emphasize the vital role of sustainability in computer science. It showcases research solutions for real-world challenges and inspires progress towards a sustainable future.
Abstract. Global ICT electricity consumption is already beyond 11 percent of the worldwide electricity production and still increasing. By 2030 it may reach around 25 percent. Previous approaches to improve efficiency and performance have often sacrificed security, leading to disastrous security issues like Meltdown and Spectre. Patching just these two vulnerabilities increases power consumption on affected computers by a seemingly harmless 5 percent. By 2030, this may be more than 1 percent of the global electricity production by just a single out of thousands of patches. This development is not sustainable, and in this talk, we will discuss both the problem and potential revolutionary solutions.
2024-10-21
Presentation
Jonas Juffinger presented at the 10th edition of hardware.io Netherlands.
2024-10-18
Research Visit
Breaking the Web’s Invisible Walls: Studying Emerging Client-Side Vulnerabilities at Scale
Invited talk by Soheil Khodayari (CISPA) and discussion on security of JavaScript-based web applications.
2024-10-16
Research Visit
Lecture by Giancarlo Guizzardi (University of Twente) “Semantic Models for Trustworthy Systems: A Hybrid Intelligence Augmentation Program”
Abstract: Cyber-human systems are formed by the coordinated interaction of human and computational components. In this talk, I will argue that these systems can only be designed as trustworthy systems if the interoperation between their components is meaning preserving. For that, we need to take the challenge of semantic interoperability between these components very seriously. I will discuss a notion of trustworthy semantic models and defend its essential role in addressing this challenge. Finally, I will advocate that engineering and evolving these semantic models as well as the languages in which they are produced require a hybrid intelligence augmentation program resting on a combination of techniques including formal ontology, logical representation and reasoning, crowd-sourced validation, and automated approaches to mining and learning.
Bio: Prof. Dr. Giancarlo Guizzardi
is a Full Professor at the University of Twente. Before joining Twente, he was a Full Professor at the Free University of Bozen-Bolzano, in the Italian Alps, where he led the Conceptual and Cognitive Modelling Research Group (CORE). Prior to that, he co-founded and co-directed the Ontology and Conceptual Modelling Research Group (NEMO) in Brazil for 10 years. He is highly active in the fields of Formal and Applied Ontology, Conceptual Modelling, Information Systems Engineering, and Enterprise Computing/Business Informatics. His research follows a multidisciplinary approach, integrating insights from Philosophy, Logics, Linguistics, and Cognitive Science to address a variety of complex challenges in these areas. He is also a Guest Professor at Stockholm University, Sweden, where he collaborates on scientific research in the fields of Value-Based Modelling, Formal and Applied Ontology in Cyber-Social Systems, and Ethical Requirements for Information Systems.
Prof. Guizzardi has published approximately 400 papers and has taken on key leadership roles in major conferences within his fields, such as ER, FOIS, IEEE CBI, and EDOC. He has served as Program Committee Chair, General Chair, Steering Committee Member, and Keynote Speaker at prominent events including ER, BPM, CAiSE, and IEEE ICSC. Currently, he is an Associate Editor for the journals Applied Ontology, Data & Knowledge Engineering, and Enterprise Modelling and Information Systems Architectures. He also serves on the Advisory Board of the International Association for Ontologies and its Applications (IAOA). In addition to his academic work, Prof. Guizzardi has led numerous technology transfer projects in areas such as Telecommunications, Risk Management, e-Government, Digital Journalism, Complex Media Management, Distributed Software Development, and Energy, among others.
2024-10-15
Lecture
Empowering Innovation: Unlocking the Potential of Privacy-Enhancing Technologies
Lecture by Prof. Dominique Schröder (TUW).
2024-10-07
Outreach to society
Happiness is endless in research
Prof. Laura Kovács shares insights from her diverse academic journey and emphasizes the importance of overcoming challenges for young researchers in her interview with Romanian Nőileg Magazine. She highlights the value of adaptability and openness to opportunities, stressing the significance of curiosity and finding joy in one’s work. Kovács encourages early-career scientists, particularly women, to embrace the challenges of research and pursue their interests with confidence. She also underscores the need for persistence in the competitive field of IT, noting the excitement of creating something new.
September 2024
2024-09-27
Research Visit
Lecture by Ruzica Piskac (Yale University) “Proofs as Polynomials”
Location: TU Wien, FAV Hörsaal 1 Helmut Veith (Favoritenstr. 11, Room HEEG02)
Date/Time: 2024-09-27 9:00 - 10:00
Abstract: Zero-knowledge (ZK) protocols are well-known cryptographic primitives that allow one party to prove to another party a statement without revealing anything beyond the statement. A ZK protocol consists of two parties: a “prover” and a “verifier”. In our work, the prover holds a secret formula and its proof of validity and needs to convince the verifier about the correctness of the proof. The verifier validates the prover’s claims, by checking every step of the proof. To be able to do that without revealing any details about the formula, we use so-called commitment schemes. Commitment schemes are a fundamental part of zero-knowledge protocols as they allow a prover to commit to a value while keeping it hidden, ensuring the value cannot be altered later. A polynomial commitment scheme can be used to commit polynomials and prove the properties of the polynomials. Our work encodes proofs as polynomials and transforms this way checking the proofs steps into checking relations between polynomials. By doing these, we are able to verify the proof without revealing the formulae (and the proof itself).
In this talk, we focus on proofs for formulas produced in the verification process and we explain how to encode them as polynomials. Initially, we developed a protocol for validating the unsatisfiability of Boolean formulas in privacy-preserving settings. We use the resolution calculus to produce a proof of unsatisfiability: we encoded each clause appearing in the proof as a polynomial and we reduced checking the correctness of the resolution rule to checking the divisibility of two polynomials.
A natural extension of this technique is to consider more expressive logics, such as those supported by SMT (Satisfiability Modulo Theories) solvers. To this end, we extended our initial work and developed a virtual machine for validating general unsatisfiability proofs. This virtual machine can support the majority of popular theories when proving program safety while being complete and sound. To demonstrate this, we use theories of equality and linear integer arithmetic as examples. These theories require non-trivial checking procedures and we proposed optimized arithmetizations based on multiset interpretation and polynomial encodings.
Finally, we will conclude the talk by outlining how this approach benefits and empowers the verification process: we can now obtain privacy while preserving correctness.
Bio: Ruzica Piskac is a Professor of Computer Science at Yale University, where she leads the Rigorous Software Engineering (ROSE) group. Her research interests span the areas of software verification, security and applied cryptography, automated reasoning, and code synthesis. Much of her research has focused on using formal techniques to improve software reliability and trustworthiness. Piskac joined Yale’s Department of Computer Science in 2013. She was previously an Independent Research Group Leader at the Max Planck Institute for Software Systems in Germany. Her research has received a range of professional honors, including multiple Amazon Research Awards, Yale University’s Ackerman Award for Teaching and Mentoring, the Facebook Communications and Networking Award, and the Microsoft Research Award for the Software Engineering Innovation Foundation (SEIF). In 2019, Yale named Piskac the Donna L. Dubinsky Associate Professor of Computer Science. Piskac holds a Ph.D. from the Swiss Federal Institute of Technology (EPFL), where her dissertation won the Patrick Denantes Prize. Her current and recent professional activities include service as Program Chair of the 37th International Conference on Computer Aided Verification and the Steering Committee of the Formal Methods in Computer-Aided Design conference. Piskac has graduated five PhD students, four of them are currently holding a position of an assistant professor of computer science.
2024-09-27 Female Mentoring Session
During an informal talk, Prof. Ruzica Piskac, Professor of Computer Science at Yale University and leader of the Rigorous Software Engineering (ROSE) group, shared her personal journey in computer science, emphasizing the challenges she faced and how she overcame them. The discussion also explored the current state of female representation in formal methods, computer science, and software engineering. Participants asked questions and shared their own experiences. Held in a warm and relaxed atmosphere, the conversation, moderated by Laura Kovacs, provided a wonderful opportunity not only to exchange insights but also to network.
2024-09-23 Summer School
Graz Security Week 2024 will be hosted by the IAIK – the Institute of Applied Information Processing and Communication at Graz University of Technology. The cybersecurity summer school is aimed at graduate students interested in security, privacy, and correctness. The main topics of the school this year include Cryptography & Cryptographic Implementations, Side Channels Privacy, and Safe AI. The program is available and registration is now open . Join us!
2024-09-18
Presentation
Florian Holzbauer delivered a presentation at the 20th ICT Security Conference
, organized by the Austrian Armed Forces.
Title. Two Years of War in Ukraine: An Analysis on Churn, Outages and Rerouting of the Internet in Kherson.
Abstract. The Internet is a key infrastructure for communication, and kinetic warfare destroys national infrastructure, including the Internet. This paper investigates the impact of Russia’s full-scale invasion on the Internet in Kherson oblast, situated in the south of Ukraine. This region is insofar of interest as it was occupied by the Russian Federation in March 2022 and partly liberated again by Ukraine in November 2022. Therefore, we rely on our active measurement campaign, probing the Ukrainian address space at an interval of two hours ever since March 5th, 2023, the 10th day of the invasion, and combine it with other data sources like geolocation, Liveuamap, and BGP data. Based on our results, we conclude that IP addresses leave Kherson oblast for other parts of Ukraine, presumably to remain reachable. In Russian-occupied regions of Ukraine, regional networks are, possibly under duress, connected with Russian state-operated networks. This regains connections at the cost of increased round-trip times and, far worse, submits Ukrainian citizens to Russian censorship. At the same time, networks operated from Ukrainian-controlled territories like Kyiv experience full outages in the affected region.
2024-09-05
Achievement
Best Paper Award at the Conference on Cryptographic Hardware and Embedded Systems (CHES)
Johannes Haring, Vedad Hadžić and Roderick Bloem won the Best Paper Award at CHES 2024 with their paper “Closing the Gap: Leakage Contracts for Processors with Transitions and Glitches ”
August 2024
2024-08-25
Outreach to society
Dagstuhl Seminar 24351
Daniel Gruss and Jonas Juffinger, both from TU Graz, participated in the Dagstuhl Seminar 24351 on Power, Energy, and Carbon-Aware Computing on Heterogeneous Systems (PEACHES). This seminar convened leading experts from computer science, software engineering, and environmental sustainability to address pressing issues at the intersection of technology and environmental impact. The main focus was on innovative methods for achieving carbon transparency, net-zero carbon goals in AI and machine learning, and carbon-aware computing strategies across different tech domains. The seminar also featured a hackathon led by Jonas Juffinger, which focused on CPU undervolting as a technique to reduce energy consumption by up to 20% without impacting system performance. The hackathon allowed participants to experiment with undervolting settings to understand its impact on system reliability and security, including potential security vulnerabilities like cryptographic key theft.
2024-08-16 Presentation
Stefan Gast contributed to three papers that will be presented at the 33rd Usenix Security Symposium
, which is focused on the latest security and privacy developments in computer systems and networks.
In the paper “Divide and Surrender: Exploiting Variable Division Instruction Timing in HQC Key Recovery Attacks”
authors R. L. Schröder, S. Gast, and Q. Guo identify a critical side-channel vulnerability in the Hamming QuasiCyclic (HQC) algorithm. This vulnerability stems from the variable execution times of division instructions affected by the modulo operator. The paper introduces a technique called DIV-SMT, designed for processors with Simultaneous Multithreading (SMT), which precisely measures these timing variations to create a highly accurate Plaintext-Checking (PC) oracle. This innovative method enables rapid recovery of HQC secret keys, drastically reducing both the time and number of queries required compared to traditional methods. For successful exploitation, the attacker must be on the same physical core as the victim. The effectiveness of this approach was demonstrated on an AMD Zen2 machine.
The paper “SnailLoad: Exploiting Remote Network Latency Measurements without JavaScript”
by the TU Graz research team introduces SnailLoad, a novel side-channel attack leveraging network latency to infer user activities on a computer without the need for direct access to network traffic. Unlike traditional side-channel attacks that typically require the attacker to directly monitor network traffic, such as through a person-in-the-middle (PITM) attack or by being in close proximity to WiFi signals, SnailLoad only necessitates that the victim loads assets from an attacker-controlled server. This method utilizes network latency fluctuations as a side channel to detect activities like video watching or website browsing. “The main threat here is that any TCP server can stealthily obtain latency traces from any clients connecting to it,” explained Stefan Gast to SecurityWeek
. The research team has further expanded public understanding of this threat by launching a dedicated website
that offers a detailed description and a live demonstration of SnailLoad, providing real-world insights into how the attack functions.
The capability of hackers to spy on individuals through any device connected to the internet has captured considerable media attention. The Independent
warns that SnailLoad effectively bypasses conventional security measures such as firewalls and VPNs. “When the victim accesses a website, watches an online video, or speaks to someone via video, the latency of the internet connection fluctuates in a specific pattern that depends on the particular content being used,” Stefan Gast further detailed. Testing showed that the researchers could spy on users watching videos with a 98% success rate, with the method proving particularly effective when the internet connection was slow and the videos were of substantial size.
More media coverage about SnailLoad is available through the following links: DER STANDARD
, heise online
.
At the symposium, the paper titled “SLUBStick: Arbitrary Memory Writes through Practical Software Cross-Cache Attacks within the Linux Kernel”
by L. Maar, S. Gast, M. Unterguggenberger, M. Oberhuber, and S. Mangard will also be presented.
2024-08-14
Research Visit
Lecture by Nikos Vasilakis (Brown University) “Security in a World of Software Supply-Chain Vulnerabilities”
Date/Time: 2024-08-14 11:00 ‒ 12:00
Location: TU Wien, FAV Hörsaal 2 (Favoritenstr. 9-11, Erdgeschoß, Room HEEG03)
Date/Time: 2024-08-19 15:00 ‒ 16:00
Location: TU Graz, IAIK seminar room (IFEG042), Inffeldgasse 16a
Abstract: Modern software incorporates thousands of third-party components. Bugs or security vulnerabilities in these components can seriously compromise the integrity of incorporating applications. Because of their widespread use, and the difficulty of vetting the enormous number of integrated components for vulnerabilities, they comprise a compelling target for attackers, who purposefully insert vulnerabilities into widely used components with the goal of compromising the integrity of entire software ecosystems. I will present a series of systems that leverage component boundaries to offer automated solutions to vulnerabilities that appear in the software component supply chain. These solutions leverage system- and language-level containment techniques to prevent different classes of attacks from affecting these applications and the broader system in which they execute. Combined, they provide a holistic and in-depth transformation-based approach to securing software ecosystems.
Bio: Nikos Vasilakis is an Assistant Professor of Computer Science at Brown University. His research encompasses systems, programming languages, and security — and has been recognized by several distinguished paper awards. His current focus is on automatically transforming systems to add new capabilities such as parallelism, distribution, and security — against a variety of threat models. Nikos is also the chair of the Technical Steering Committee behind PaSh, a shell-script optimization system hosted by the Linux Foundation.
2024-08-06
Lecture
Laura Kovács delvers a lecture “First-Order Theorem Proving” at Marktoberdorf Summer School 2024
First-order theorem proving is one of the earliest research areas within artificial intelligence and formal methods. It is undergoing a rapid development thanks to its successful use in program analysis and verification, security analysis, symbolic computation, theorem proving in mathematics, and other related areas. Breakthrough results in all areas of theorem proving have been obtained, including improvements in theory, implementation, and the development of powerful theorem proving tools. However, recent developments are not always easily accessible to non-specialists. This mini-lecture series presents the theory and practice behind the development of powerful theorem proving tools. The workhorse used for a demonstration of concepts discussed at the tutorial will be our theorem prover Vampire. The tutorial will first focus on practicalities while using first-order Vampire for validating mathematical theorems. We will then further introduce the core concepts of automating first-order theorem proving in first-order logic with equality. We will discuss the resolution and superposition calculus, introduce the saturation principle, present various algorithms implementing redundancy elimination, and demonstrate how these concepts are implemented in Vampire.
July 2024
2024-07-08
Presentation
Stefano Trevisani presented at the 37th IEEE Computer Security Foundations Symposium (CSF 2024)
Title. On Efficient and Secure Compression Functions for Arithmetization-Oriented Hashing
Abstract. ZK-SNARKs, a fundamental component of privacyoriented payment systems, identity protocols, or anonymous voting systems, are advanced cryptographic protocols for verifiable computation: modern SNARKs allow to encode the invariants of a program, expressed as an arithmetic circuit, in an appropriate constraint language from which short, zero-knowledge proofs for correct computations can be constructed. One of the most important computations that is run through SNARK systems is the verification of Merkle tree (MT) opening proofs, which relies on the evaluation of a fixed-input-length (FIL) cryptographic compression function over binary MTs. As classical, bit-oriented hash functions like SHA-2 are not compactly representable in SNARK frameworks, Arithmetization-Oriented (AO) cryptographic designs have emerged as an alternative, efficient solution. Today, the majority of AO compression functions are built from permutation-based hashing modes, such as Sponge. While this approach allows cost savings, compared to blockcipher-based modes, as it does not require key-scheduling, AO blockcipher schedulers are often cheap to compute. Furthermore, classical bitoriented cryptography has long studied how to construct provably secure compression functions from blockciphers, following the Preneel-Govaerts-Vandewalle (PGV) framework. The potential efficiency gains together with the strong provable security foundations in the classic setting, motivate the study of AO blockcipher-based compression functions. In this work, we propose AO PGV-LC and PGV-ELC, two AO blockcipher-based FIL compression modes inspired by and extending the classical PGV approach, offering flexible input and output sizes and coming with provable security guarantees in the AO setting. We prove the collision and preimage resistance in the ideal cipher model, and give bounds for collision and opening resistance over MTs of arbitrary arity. We compare experimentally the AO PGV-ELC mode over the HADES blockcipher with its popular and widely adopted Sponge instantiation, POSEIDON, and its improved variant POSEIDON2. Our resulting constructions are up to 3× faster than POSEIDONAND 2× faster than POSEIDON2 in native x86 execution, and up to 50% faster in the Groth16 SNARK framework. Finally, we study the benefits of using MTs of arity wider than two, proposing a new strategy to obtain a compact R1CS constraint system in such case. In fact, by combining an efficient parametrization of the HADES blockcipher over the PGV-ELC mode, together with an optimal choice of the MT arity, we measured an improvement of up to 9× in native MT construction time, and up to 2.5× in proof generation time, compared to POSEIDON over binary MTs.
2024-07-06
Workshop
Asynchronous Hyperproperties: from Theory to Practice
Hyperproperties are a general framework to reason about properties requiring comparing multiple system executions, like security properties or robustness requirements. In this workshop, we want to bring together practitioners from different backgrounds with theoreticians developing frameworks for specifying hyperproperties.
The workshop format will focus on discussions and promoting the interchange of ideas between different communities.
Find more information at the Workshop site
, CySec News
.
2024-07-05
Research Visit
Lecture by Sven Bugiel (CISPA Helmholtz Center for Information Security) “Access Control in Mobile Software Stacks: Can we do fundamentally better?”
Abstract: A cornerstone of mobile privacy and security is the permission system that enables users to selectively grant or revoke apps’ access to data. This pivotal role of permissions has earned them a lot of attention over the last 15 years by the research community, who identified its shortcomings and suggested improvements to it. In this talk, we briefly recap the access control model of the permission system “under the hood” and then take a step back to question whether we can do fundamentally better at the system design level. Central to this question is the existence of an ambient authority as the root of many problems and how we can get rid of it. To give food for thought, we base this discussion on a recent research work that proposes object capabilities as alternative access control model for Android and on looking at Google Fuchsia, Google’s latest operating system that is capability-based. We present some early results that show that even Fuchsia’s design is still not a sufficient solution and what the challenges are for such a paradigm shift in access control for (mobile) software stacks.
Bio: Sven Bugiel is a security researcher focusing on (mobile) operating system security and trusted computing. In the past, he was particularly looking into mandatory access control systems for the Android OS and integrating hardware security building blocks into mobile operating systems. This interest has extended to object-capability systems and developing new confidential computing solutions. More recently, he also worked on the intersection of those topics with human-centered studies, authentication, and data science. Sven is a tenured faculty at the CISPA Helmholtz Center for Information Security in Saarbrücken, Germany since end of 2021.
June 2024
2024-06-24
Research Visit
Lecture by Konrad Rieck (TU Berlin, Guest Professor at TU Wien) “On Challenges in Defending Against Code Stylometry”
Location: TU Wien, FAV Hörsaal 1 Helmut Veith (1040 Vienna, Favoritenstr. 9-11, Erdgeschoß, Room HEEG02)
Time: 16:00 – 17:00
Abstract: Source code often contains subtle stylistic patterns that can be used to identify its developer, an approach known as code stylometry. While a series of research has shown that code stylometry can recognize one programmer among hundreds of others, defenses against this approach have received little attention so far. In this talk, we address this research gap from two perspectives. First, we introduce a method for automatically imitating programming styles through semantic-preserving transformations. This method allows us to mislead correct identification and protect developers’ privacy. Second, however, we prove that true anonymity cannot be achieved in this way and that stylistic patterns remain in source code under realistic conditions. Our results thus underscore the need for raising awareness and further research into protecting developers’ privacy.
Bio: Konrad Rieck is a Professor of Computer Science at TU Berlin, where he heads the Chair of Machine Learning and Security within the Berlin Institute for the Foundations of Learning and Data. Additionally, he is a Guest Professor at TU Wien. Previously, Konrad has been working at TU Braunschweig, University of Göttingen, and Fraunhofer Institute FIRST. His research interests revolve around computer security and machine learning. His group is developing novel methods for detecting computer attacks, analyzing malicious software and discovering security vulnerabilities. Moreover, the group explores the security and privacy of learning algorithms. Konrad is also interested in efficient algorithms for analyzing structured data, such as strings, trees, and graphs. His Erdős number is 3 (Müller → Jagota → Erdős) and his Bacon number is ∞. He is a very distant academic relative of Carl Friedrich Gauß (see here), although this doesn’t help when solving math problems.
2024-06-19
Outreach to society
Chat control is a security risk for all of Europe
Matteo Maffei (TU Wien), Daniel Gruss (TU Graz), Krzysztof Pietrzak (ISTA), and René Mayrhofer (Johannes Kepler University Linz), in a dialogue with DER STANDARD, have expressed significant concerns about the proposed client-side scanning measures in the EU.
As the European Parliament reviews the child sexual abuse (CSA) prevention and combat regulation, which advocates for the preemptive scanning of messages in platforms like WhatsApp, a broad spectrum of stakeholders, including researchers, data protection organizations, and child protection centers, have raised alarm. Critics argue that this method risks compromising secure communication, exposing citizens to extensive surveillance, and potentially allowing misuse by state actors or criminals. Additionally, there is apprehension about the arbitrary classification of content as illegal, which may encroach upon freedoms such as political speech. If enforced, this policy could fundamentally alter the operation of messaging services across Europe. Encrypted services like Signal might exit the European market, while others, such as WhatsApp and Threema, could be compelled to lower their encryption standards to align with new EU regulations.
Daniel Gruss pointed out the inherent security weaknesses in client-side scanning software, noting that such systems, once deployed, are bound to harbor exploitable flaws due to their complexity. Matteo Maffei emphasized the profound impact on fundamental rights, likening the scanning process to an invasive system where every letter is read, verified, and resealed before delivery. He argued that using client-side scanning to break encryption carries huge risks that could threaten the security of all citizens.
Highlighting the importance of maintaining robust communication security, the experts advocate for more research into bolstering system security rather than diminishing it, underscoring that secure communication is a critical and well-understood pillar of IT security that must be preserved.
Find the full text of the article in German on DER STANDARD
.
2024-06-11
Research Visit
Automatic On-Device Mitigation for Crypto API Misuse
Invited talk by Florian Draschbacher (TU Graz) and discussion on automatic on-device mitigation for crypto API misuse in Android applications.
2024-06-11
Achievement
Best Paper Award at HOST 2024
The paper titled “Security Aspects of Masking on FPGAs,” authored by Barbara Gigerl, Kevin Pretterhofer, and Stefan Mangard, was honored with the Best Paper Award at the IEEE International Symposium on Hardware Oriented Security and Trust (HOST) 2024.
2024-06-03
Research Visit
Formal Verification of Probe Isolating Non-Interference in Secure Circuits
TUW hosted an enriching full-day session led by SPyCoDe PIs, Laura Kovács and Roderick Bloem, focusing on the advanced topic of formal verification of probe isolating non-interference (PINI) in secure circuits. The meeting featured distinguished expert Dr. Nikolaj Bjorner from Microsoft Research, renowned for his work with the advanced SMT (Satisfiability Modulo Theories) constraint solver Z3, who contributed unique insights and expertise. Other participants included Clemens Eisenhofer and Robin Coutelier. Throughout the day, the group explored how SMT reasoning could be expanded to enhance the security features of electronic circuits, effectively increasing their resistance to various forms of interference and tampering, both with and without the use of probabilities. This event not only showcased the latest advancements in secure circuit design but also promoted collaboration among some of the brightest minds in the field. It was a day filled with stimulating exchanges, thought-provoking ideas, and meaningful knowledge sharing, setting the stage for further research.'
May 2024
2024-05-21
Presentation
Simon Jeanteur presented CryptoVampire at the 45th IEEE Symposium on Security and Privacy
The presentation highlighted the results of collaborative research with Laura Kovács, Matteo Maffei, and Michael Rawson. CryptoVampire represents a significant breakthrough in protocol verification, enabling the first fully automated proofs via the innovative Computationally Complete Symbolic Attacker (CCSA) model. This advancement considerably strengthens the capabilities for automatic verification of protocols, employing a more sophisticated model than was previously possible.
2024-05-21
Presentation
Florian Holzbauer and Jakob Rosenblattl presented their research during the Poster Session at TMA Conference.
Florian Holzbauer and Jakob Rosenblattl presented their research via posters at both the 12th TMA PhD School ‘Traffic Management and Analysis at All Layers’ and the main Network Traffic Measurement and Analysis (TMA) Conference. This opportunity allowed them to connect with experts and peers within the measurement research community.
Florian Holzbauer’s poster focused on IPv6 reconnaissance using ICMPv6 error messages, while Jakob Rosenblattl showcased work on topology discovery within the Bitcoin network.
The conference’s emphasis on network traffic measurement and analysis offered valuable insights into current research challenges. They engaged with cutting-edge topics such as eBPF, machine and deep learning for network analysis, and emerging attacks targeting IoT devices, enriching their knowledge and research perspectives.
2024-05-02
Research Visit
Lecture by Yuval Yarom (Ruhr University Bochum) “About time for cache attacks”
Location: TU Graz, Showroom (DHEG136E), Sandgasse 36 (ground floor)
Time: 13:00 – 14:00
Abstract: Over the last two decades, cache attacks have emerged as a significant threat to shared computing. At their core, cache attacks exploit minute timing variation to query the state of a cache in the computer. From this cache state, the attacker can infer secret data processed by victim software that uses the shared cache. As these attacks often measure minute variations, at the order of few nanoseconds, multiple proposed defences aim at depriving attackers of high-resolution clocks.
In this talk we show the futility of such attempts. We first show that coarse-grained cache attack can retrieve sensitive information even in the absence of high-resolution timers. We then delve deeper into the nature of cache attacks, demonstrating that they allow arbitrary computation on cache state. Finally, we show how attackers can exploit this observation to implement high-frequency, high-resolution cache attacks without using high-resolution timers.
Bio: Yuval Yarom
is a professor at Ruhr University Bochum, where he leads the Chair for Computer Security. He earned his Ph.D. in Computer Science from the University of Adelaide in 2014, and an M.Sc. in Computer Science and a B.Sc. in Mathematics and Computer Science from the Hebrew University of Jerusalem in 1993 and 1990, respectively. In between he has been the Vice President of Research in Memco Software and a co-founder and Chief Technology Officer of Girafa.com.
Yuval’s research explores the security of the interface between the software and the hardware. In particular, he is interested in the discrepancy between the way that programmers think about software execution and the concrete execution in modern processors. He works on identifying micro-architectural vulnerabilities, and on exploitation and mitigation techniques.
April 2024
2024-04-29
Research Seminar
VIRAS: A Conflict-Driven Descision Procedure for mixed Integer-Real Arithmetic
2024-04-23
Public Lecture
Martina Lindorfer delivered a lecture at the Cluster of Excellence CASA
Shedding Light on Data Collection and Security Issues in Modern Apps
.
Abstract. Mobile phones are an integral part of every aspect of our daily lives and we use them, through a plethora of apps, for everything from communicating, to shopping and banking, to controlling the devices in our smart homes. With the goal of maximizing user experience, apps collect and process an increasing amount of private information. With the rising popularity of IoT devices, we often give up even more private information about our daily lives and habits for the sake of the convenience.
This private information has become a commodity: tech monopolies and shadow brokers collect and aggregate data, not only to provide tailored content, but also for market research and targeted advertising. This process is far from transparent and our data is not always in trustworthy and secure hands. Even developers with the best intentions are faced with supply chain issues when integrating libraries, external tools, and services. While existing legislation like the GDPR, CCPA, and upcoming ones like the Cyber Resilience Act aim to protect consumers against privacy invasions and insecure products, the required techniques for automated technical analyses for their enforcement remain an open challenge.
In this talk, I will present our ongoing research on developing scalable static and dynamic program analysis techniques for modern mobile and web-based apps, including their integration with IoT devices, for large-scale measurements to enable transparency and accountability in the way apps process and share private information. I will also discuss while recent privacy developments by Apple and Google seemingly increase transparency, there remains a lack of enforcement and accountability when it comes to how apps handle our data. Finally, I will touch on how new app programming paradigms break expected security and privacy guarantees.
Video
2024-04-22
Outreach to society
Prof. Martina Lindorfer was interviewed by the “Wiener Zeitung“
Prof. Martina Lindorfer and Prof. Stefan Neumann discuss Google’s 25-year dominance and its effects on competition and information accessibility in Mathias Ziegler’s article “Wie böse ist Google wirklich?“ (“How evil is Google really?“) featured in Wiener Zeitung.
2024-04-17
Research Visit
Lecture by Nikolaj Bjorner (Microsoft Research) “Formal Methods at Microsoft: Secure and Reliable Programs for Everyone, Everywhere”
Location: TU Wien, Campus Freihaus, Informatikhörsaal (1040 Vienna, Treitlstraße 3)
Time: 13:00 – 13:45
Abstract: The talk presents several research projects and tools from Microsoft Research and their impact on programming secure and reliable systems. As a common basis they take a formal methods angle where systems are viewed as mathematical objects. For the context of this talk we consider computation through lenses of calculi and measurements. We then describe how these research threads interleave with major developments from academic research and phase shifts in industry. With Microsoft rapidly pivoting on deploying and delivering AI products the talk relates the foundations with recent and current projects, including development of provably secure systems, securing smart contracts, network verification, efficient and correct compilation for ML systems, and programming systems and runtimes for interacting with AI.
Bio: Dr. Nikolaj Bjorner is a partner researcher at Microsoft Research. Nikolaj’s main line of work is around the state-of-the-art SMT constraint solver Z3. Z3 was developed with Leonardo de Mour:a, Lev Nachmanson and Christoph Wintersteiger. Z3 is used for program verification, test case generation among several applications. The work around Z3 has received several awards. Karthick Jayaraman and Nikolaj created the SecGuru tool that is used to validate firewalls and routing configurations for Microsoft Azure. In 2021 Nikolaj Bjorner was named an ACM Fellow
2024-04-17
Research Visit
Lecture by Byron Cook (UCL, Amazon) “The Business of Proof”
Location: TU Wien, Campus Freihaus, Informatikhörsaal (1040 Vienna, Treitlstraße 3)
Time: 11:15 – 13:00
Abstract: With only a few niche exceptions, the software industry had not previously figured out how to make deep use of formal mechanical reasoning based on mathematical logic. At Amazon we have recently seen tremendous adoption of the approach by product groups, with a variety of customer-facing launches that use automated reasoning, and numerous internal proof projects. This talk describes those projects, and tries explain what went well at Amazon. The talk also describes challenges that we face to scale the approach to the next level.
Bio: Dr. Byron Cook , FREng is Professor of Computer Science at University College London (UCL). Byron is also Vice President and Distinguished Scientist at Amazon. Byron’s has worked in a variety of areas over the years, including computer/network security, program analysis/verification, programming languages, theorem proving, hardware design, operating systems, and biological systems.
2024-04-15
Research Seminar
Efficient and Secure Compression Functions for Arithmetization-Oriented Hashing
2024-04-01
Outreach to society
Why We Will Never Get Rid of Side Channels
In the April episode of the “What That Means” InTechnology Podcast, Daniel Gruss discusses with hosts Camille Morhardt and Anders Fogh (Intel) the balance between side channels and resource sharing, common challenges and how to manage them, the impact of AI on side channels, and securing critical infrastructure stored in space. Find more on YouTube .”
March 2024
2024-03-26
Research Visit
Lecture by Reiner Hähnle (TU Darmstadt) “Context-aware Trace Contracts.”
Abstract: The behavior of concurrent, asynchronous procedures depends in general on the call context, because of the global protocols that govern scheduling. This context cannot be specified with the state-based Hoare-style contracts common in deductive verification. Recent work generalized state-based to trace contracts, which permit to specify internal behavior of a procedure, such as calls or state changes, but not its call context. In this talk we discuss a program logic of context-aware trace contracts for specifying global behavior of asynchronous programs. We also provide a sound proof system that addresses two challenges: First, to observe the program state not merely at the end points of a procedure, we introduce the novel concept of an observation event. Second, to combat combinatorial explosion of possible call sequences of procedures, we adapt Liskov’s principle of behavioral subtyping to the analysis of asynchronous calls.
This is a joint work with Eduard Kamburjan (U Oslo) and Marco Scaletta (TU Darmstadt).
Bio: Reiner Hähnle is Professor in Software Engineering at the Computer Science Department of TU Darmstadt. He has wide-ranging interests in the formal foundations of software design, of programming languages, and of quality assurance by verification. He is co-initiator of the KeY project that maintains the well-known, eponymous Java verification tool and he is co-designer of the active object language ABS. He is co-founder of the Tableaux and IJCAR conference series and currently SC Chair of FASE. Notably, he was the first ever Wine Chair of an international Computer Science conference at ECOOP 2014.
2024-03-04
Research Seminar
Comparing Apples to Androids: Discovery, Retrieval, and Matching of iOS and Android Apps for Cross-Platform Analyses
February 2024
2024-02-08
Research Visit
Lecture by Andrea Basso (University of Bristol) “New Techniques for Efficient Isogeny-based Encryption Protocols”
Location: TU Graz, IAIK seminar room (IFEG042), Inffeldgasse 16a
Time: 13:30 – 14:30
Abstract: Isogeny-based cryptography is known for its low bandwidth requirements, which often come at the cost of slower computations. SIDH, one of the most well-known isogeny-based key exchanges, and the only one submitted to the NIST standardisation process, was broken in 2022 in a series of three breakthrough papers. The attack relies on isogenies between abelian varieties (a generalisation of elliptic curves to higher dimensions), and it leads to a complete key recovery within seconds.
In this talk, we discuss two approaches to obtaining secure protocols that could, eventually, replace SIDH. The first approach involves modifying the SIDH protocol to include simple but effective countermeasures against all known attacks. The technique is based on restricting the set of potential isogenies, so that less information about the secret isogeny (in the form of torsion images) need to be revealed.
The second approach is based on the development of a new PKE, which we call FESTA. The attacks on SIDH rely on higher-dimensional isogenies to make some computations, previously believed to be hard, extremely efficient. In FESTA, we use the same techniques constructively: we build a trapdoor function where the inversion operation consists of recovering an SIDH secret key. From the trapdoor, it is then simple to obtain an IND-CCA PKE through standard transformations.
Bio: Andrea Basso is a postdoctoral researcher at the University of Bristol, where he focuses on developing new isogeny-based protocols, with a particular interest in advanced functionalities such as non-interactive key exchanges and oblivious pseudorandom functions. He received his PhD from the University of Birmingham, and he will soon join IBM Research Zurich as a postdoctoral researcher.
January 2024
2024-01-15
Research Seminar
Secure implementation of the masking countermeasure on different platforms
2024-01-15
Research Visit
Lecture by Thomas Schneider (Technical University of Darmstadt) “Recent Advances in Secure Two-Party Computation”
Location: TU Graz, seminar room DHEG045 (Data House) Time: 16:00 – 17:00
Abstract: Secure two-party computation allows two parties to securely compute a function on their respective private inputs. It allows to preserve privacy in applications that involve a client and a single server, and in settings where private data is outsourced to two non-colluding servers. In this talk, I will give an overview on recent advances in the area of secure two-party computation. In particular, I will focus on the setting with semi-honest parties, which allows to construct the most efficient protocols. I will summarize three recent research results from the ENCRYPTO group: First, circuit synthesis and secure evaluation of circuits should be considered together to not leak private information when evaluating malformed circuits with popular instantiations of Yao’s garbled circuits protocol (JoC'23). In the area of secret-sharing based protocols, ABY2.0 (USENIX Security’21) allows highly efficient secure evaluation of Boolean circuits with multi-input AND gates and vector products, and FLUTE (IEEE S&P’23) extends these results to multi-input lookup tables. Among many other applications, these protocols substantially improve efficiency of privacy-preserving machine learning.
Bio: Thomas Schneider is full professor for Cryptography and Privacy Engineering in the Department of Computer Science at Technical University of Darmstadt, Germany. Before, he was independent research group leader at TU Darmstadt (2012-2018), did a PhD in IT Security at Ruhr-University Bochum (2008- 2011), and wrote his Master thesis during a research internship at Nokia Bell Labs, NJ, USA (2007). His research focuses on privacy, cryptographic protocols, applied cryptography, and computer security. He heads the Cryptography and Privacy Engineering Group (ENCRYPTO), whose mission is to demonstrate that privacy can be efficiently protected in real-world applications. For this, his group combines applied cryptography and algorithm engineering to develop cryptographic protocols and tools for protecting sensitive data and algorithms. For his research on cryptography and privacy engineering, he was awarded with an ERC Starting Grant 2019 and an ERC Consolidator Grant 2023.
December 2023
2023-12-13
Research Visit
Lecture by Frank Leymann (Universität Stuttgart) “Post-Quantum Security.”
Abstract: We remind the underpinnings of classical encryption, factorization and elliptical curves, and their relation to discrete logarithms. After very briefly sketching the key resources of quantum computing, Shor’s algorithm is revealed to solve the discrete logarithm problem. Thus, quantum computing is jeopardizing today’s cryptographic infrastructure. Lattice-based cryptography is introduced, and a brief overview on Dilithium and Kyber is given. These two algorithms are believed to be quantum safe, i.e. they promise to resist attacks by quantum (as well as classical) algorithms. While Dilithium and Kyber are already being standardized, a broad understanding of the above security threads is missing in industry. A sketch of activities of major industry players closes the talk.
Bio: Frank Leymann is the first Kurt Gödel Visiting Professor and an honorary professor at TU Wien. He studied Mathematics, Physics, and Astronomy at the University of Bochum, Germany. After receiving his master’s degree in 1982, he pursued his PhD in Mathematics in 1984. Afterwards, he joined IBM Research and Development and worked for two decades for the IBM Software Group. In 2004, Frank Leymann was appointed as a full professor of computer science at the University of Stuttgart, where he founded the Institute of Architecture of Application Systems and serves as its director. His research interests encompass middleware in general, pattern languages, and cloud computing, with a current strong focus on quantum computing. Frank is an elected member of the Academy of Europe (Academia Europaea). He published uncountable papers in journals and proceedings, co-authored four textbooks, and holds more than 70 patents, especially in the area of workflow management and transaction processing. He served on steering-, program- and organization committees of many international conferences, and is (associated) editor of several journals. From 2006 to 2011, he was a member of the scientific directorate of Schloss Dagstuhl (Leibniz Center of Computer Science). In 2019, he was appointed as a Fellow at the Center of Integrated Quantum Science and Technology (IQST), and in 2020 he was appointed as Member of the Expert Council for Quantum Computing of the German Government.
2023-12-01
Research Visit
Invited talk by Michele Orrù (Sorbonne Université) “Elastic SNARKs for Diverse Environments.”
Abstract: We introduce and study elastic SNARKs, a class of proofs where the prover can select different time and memory tradeoffs, depending on the execution environment and the proved statement. The output proof is independent of the chosen configuration. We construct an elastic SNARK for rank-1 constraint satisfiability (R1CS). In a time-efficient configuration, the prover uses a linear number of cryptographic operations and a linear amount of memory. In a space-efficient configuration, the prover uses streaming algorithms and a quasilinear number of cryptographic operations with a logarithmic amount of memory. A key component of our construction is an elastic probabilistic proof. Along the way, we also formulate a streaming framework for R1CS that we deem of independent interest. We additionally contribute Gemini, a Rust implementation of our protocol. Our benchmarks show that Gemini, on a single machine, supports R1CS instances with tens of billions of constraints.
Bio: Michele Orrù is a CNRS research scientist at Sorbonne Université. Previously, he was at UC Berkeley as a research scholar. He obtained his PhD from École Normale Supérieure, and his MSc in mathematics from the University of Trento. His research focuses on building authentication mechanisms that preserve user anonymity. He works on improving the efficiency and security of zero-knowledge proofs, lightweight anonymous credential systems, and confidential transactions. In the past, Michele has contributed to Python, Debian, and Tor. He co-designed GlobaLeaks, an open-source whistleblowing platform now translated into more than 90 languages and used by more than 300 organizations. Additionally, he co-authored the cryptography behind Google’s Trust Tokens. Currently, he is actively involved in maintaining the arkworks.rs algebra crate.
November 2023
2023-11-28
Presentation
SPyCoDe researchers participate in ACM CCS 2023.
Five representatives from SpyCoDe actively contributed to the ACM Conference on Computer and Communications Security (CCS) held in Copenhagen, Denmark, from November 26 to 30, 2023. This conference serves as the annual flagship event of the Special Interest Group on Security, Audit, and Control (SIGSAC) within the Association for Computing Machinery (ACM), attracting information security researchers, practitioners, developers, and users worldwide to explore cutting-edge ideas and results.
During November 27-29, the conference featured the presentation of the following research contributions:
-
CheckMate: Automated Game-Theoretic Security Reasoning by Lea Salome Brugger, Laura Kovács, Anja Petković Komel, Sophie Rain, and Michael Rawson, all from TUW, in the track “Formal Methods and Programming Languages”,
-
Let’s Go Eevee! A Friendly and Suitable Family of AEAD Modes for IoT-to-Cloud Secure Computation by Amit Singh Bhati (KU Leuven, Belgium), Erik Pohle (KU Leuven, Belgium), Aysajan Abidin (KU Leuven, Belgium, Elena Andreeva (TUW), Bart Preneel (KU Leuven, Belgium) in the track: “Applied Cryptography”,
-
Cryptographically Enforced Memory Safety by Martin Unterguggenberger, David Schrammel, Lukas Lamster, Pascal Nasahl and Stefan Mangard, all from Graz University of Technology, in the track “Software Security”,
-
IoTFlow: Inferring IoT Device Behavior at Scale through Static Mobile Companion App Analysis by David Schmidt (TUW), Carlotta Tagliaro (TUW), Kevin Borgolte (Ruhr University Bochum, Germany) and Martina Lindorfer (TUW) in the track “Network Security”.
These insightful presentations showcase SpyCoDe’s commitment to advancing knowledge and innovation in the realm of computer and communications security.
2023-11-26
Public Lecture
Martina Lindorfer joined as a speaker for the iMentor Workshop.
Individualized Cybersecurity Research Mentoring (iMentor ) Workshop co-located with the ACM Conference on Computer and Communications Security (ACM CCS) virtually. It is dedicated to attracting, mentoring, and providing career guidance to early-stage graduate students from underrepresented communities who aspire to pursue a career in computer security.
Martina gave a talk titled “IoTFlow the Making-Of: Inferring IoT Device Behavior at Scale through Static Mobile Companion App Analysis.” Using the preparation of her article presented at ACM CCS 2023 as an example, she shared with the iMentor cohort the behind-the-scenes journey of the IoTFlow paper — from its initial conception to the different iterations and revisions it underwent.
Abstract. The number of “smart” devices, that is, devices making up the Internet of Things (IoT), is steadily growing. They suffer from vulnerabilities just as other software and hardware. Automated analysis techniques can detect and address weaknesses before attackers can misuse them. Applying existing techniques or developing new approaches that are sufficiently general is challenging though. Contrary to other platforms, the IoT ecosystem features various software and hardware architectures. We introduce IoTFlow, a new static analysis approach for IoT devices that leverages their mobile companion apps to address the diversity and scalability challenges. IoTFlow combines Value Set Analysis (VSA) with more general data-flow analysis to automatically reconstruct and derive how companion apps communicate with IoT devices and remote cloud-based backends, what data they receive or send, and with whom they share it. We analyzed 9,889 manually verified companion apps with IoT-Flow to understand and characterize the current state of security and privacy in the IoT ecosystem. We discovered various IoT security and privacy issues, such as abandoned domains, hard-coded credentials, expired certificates, and sensitive personal information being shared.
2023-11-24
Research Visit
Invited talk by Christof Ferreira Torres (ETH Zurich) “Do You Trust Your Wallet? Analyzing the Privacy Risks of Web3 Wallets.”
Abstract: Blockchains are complex decentralised systems that can be divided into different layers such as peer-to-peer networking, consensus protocols, smart contracts, wallets, etc. In this talk, I will focus on the privacy aspects of Web3 wallets. With the recent hype around the Metaverse and NFTs, Web3 is getting more and more popular. The goal of Web3 is to decentralize the web via decentralized applications. Wallets play a crucial role as they act as an interface between these applications and the user. Wallets such as MetaMask are being used by millions of users nowadays. Unfortunately, Web3 is often advertised as more secure and private. However, decentralized applications as well as wallets are based on traditional technologies, which are not designed with privacy of users in mind. In this talk, we will analyze the privacy implications that Web3 technologies such as decentralized applications and wallets have on users. To this end, I will present a framework that measures exposure of wallet information. Using this framework, we studied whether information about installed wallets is being used to track users online. First, we analyzed the top 100K websites and found evidence of 1,325 websites running scripts that probe whether users have wallets installed in their browser. Second, we measured whether decentralized applications and wallets leak the user’s unique wallet address to third-parties. We intercepted the traffic of 616 decentralized applications and 100 wallets and found over 2000 leaks across 211 applications and more than 300 leaks across 13 wallets. Our study shows that Web3 poses a threat to users’ privacy and that we require new designs towards more privacy-aware wallet architectures.
Bio: Christof Ferreira Torres is a postdoctoral researcher at ETH Zurich. He is part of the Secure & Trustworthy Systems Group lead by Prof. Dr. Shweta Shinde. His research focuses on analyzing the security and privacy of distributed ledgers. He obtained a joint Ph.D. in computer science from the University of Luxembourg and the Technical University of Munich. His Ph.D. thesis focuses on the automated security assessment of smart contracts. He received the Excellent Doctoral Thesis award from the University of Luxembourg and Ripple’s Impact award for his research on the security of smart contracts. Prior to his Ph.D., he has been working as a security researcher at the Fraunhofer Institute for Applied and Integrated Security (AISEC) near Munich, Germany.
2023-11-24
Achievement
Maria Eichlseder received the Hedy Lamarr Prize from the City of Vienna.
Prof. Eichlseder was honored for her contributions to the development of new methods for cryptanalysis. She is one of the designers who developed the Ascon algorithm, which earlier this year was selected by the US National Institute of Standards and Technology (NIST) as the standard for lightweight cryptography. It also won the 2019 CAESAR competition for authenticated encryption in the lightweight applications category.
Lightweight cryptography deals with cryptographic methods that are particularly suitable for use in resource-constrained environments, such as RFID tags or sensors, due to their low resource requirements. This applies in particular to the Internet of Things with its numerous small sensors and actuators, as only little energy and power are available here. Ascon is also suitable for miniature technologies such as medical implants or keyless car openers.
Hedy Lamarr Prize recognizes female researchers in Austria for their outstanding achievements in the field of information technology. The prize is named after the Vienna-born Hollywood actress and scientist Hedy Lamarr. The award winners serve as role models for the next generation and motivate young women to pursue a career in the IT industry.
2023-11-15
Achievement
Maria Eichlseder has been awarded a prize for excellence in teaching
Maria Eichlseder, an assistant professor at IAIK, was one of the four recipients honored with a prize for excellence in teaching 2022/23 at Graz University of Technology. She received the accolade for her outstanding lecture in Cryptography.
2023-11-13
Public Lecture
Krzysztof Pietrzak gave a talk on “Sustainable Blockchains“
Tha talk is a part of the Public Lecture Series ‘Sustainability in Computer Science’ under the auspices of Informatik Austria .
Abstract. The Bitcoin blockchain achieves consensus in an open setting, i.e., where everyone can participate. This was believed to be impossible, the key idea to make this possible was to use computing power rather than some kind of identities for voting through “proofs of work”. Unfortunately, this approach is not sustainable: the Bitcoin blockchain burns roughly as much electricity as a country like Austria. We will outline sustainable alternatives for achieving a Bitcoin-like blockchain, with a focus on using disk-space instead of computation and how this is realized in the Chia Network blockchain."
2023-11-02
Presentation
Jonas Juffinger presented “CSI:Rowhammer - Cryptographic Security and Integrity against Rowhammer“ at the Hardwear.io Security Trainings and Conference 2023
.
The research addresses Rowhammer, a severe security problem in DRAM that allows an unprivileged adversary to gain kernel privileges by inducing electrical disturbance errors. CSI:Rowhammer is a hardware-software co-designed Rowhammer mitigation with principled cryptographic security and integrity guarantees, intentionally avoiding a focus on specific Rowhammer properties. Due to its generic design, the system provides protection against all Rowhammer attacks.
The presentation delved into the comprehensive details of designing a system like CSI:Rowhammer, covering aspects such as implementing low-latency hardware correction, maximizing software correction potential, securing correction routines in software against bit flips, managing possible race conditions, ensuring compatibility with virtual machines, evaluating the entire system, and more.
October 2023
2023-10-25
Outreach to society
Engaging school children and young people in STEM activities.
In two articles featured in the release of doIT 2/2023 in “Der Standard,” SpyCoDe members explore the significance of involving children in STEM activities and investigate the opportunities available in IT for the younger generation.
Sophie Rain introduces the “Abenteuer Informatik für Volksschule” initiative, where elementary school children visit the university to playfully delve into the world of algorithms. While programming education is now accessible to 8-year-old children, adapting content and delivery methods to align with their developmental needs and capabilities is essential. The TU Wien team is dedicated to creating an educational playground for primary and secondary school classes, fostering their interest in STEM. Sophie underscores the initiative’s crucial role in empowering girls to overcome stereotypes suggesting that technology is not for them.
Professor Maria Eichlseder shares her journey in establishing a successful career in IT. A small holiday project involving an encryption algorithm revealed to her the truly exciting nature of cryptography. Despite having limited prior knowledge in informatics from school, her fascination with cryptoanalysis led her to co-author Ascon, an authenticated encryption and hashing algorithm that has become an international standard. Today, Maria characterizes IT as an inspiring environment where individuals can initiate diverse projects, collaborate in dynamic teams, and contribute to their unique interests. The job landscape is expansive, featuring numerous companies and startups in Austria with promising earning potential. Addressing young people, she encourages them by stating, “Getting involved is fun and helps you develop personally!”
2023-10-12
Research Visit
Invited talk by Chrysoula Stathakopoulou (Chainlink Labs) “Build it Super Simple: Fast consensus on a DAG“
Abstract: After carefully breaking down the consensus problem, designing a protocol allowing high throughput and low-latency becomes easier than ever, if one finds the right abstraction that is both powerful and simple. This talk introduces BBCA (Byzantine Broadcast with Complete-Adopt), a novel broadcast primitive which builds on top of Consistent Broadcast an interactive Complete-Adopt API which allows nodes to probe its internal state. We discuss how to leverage BBCA to build high-throughput and low latency consensus on a DAG and show how this design evolves from state of the art DAG based protocols.
Bio: Chrysoula Stathakopoulou is a blockchain and distributed systems researcher at Chainlink Labs, passionate about decentralizing computation and trust with highly performant systems. Before joining Chainlink Labs, she worked at the blockchain group in IBM research focusing on consensus protocols. Her academic journey culminated in the successful completion of a PhD program at ETH Zurich.
2023-10-12
Achievement
Giulia Scaffino listed amongst Top 30 @ TU Wien Under 30.
In 2023, Giulia Scaffino (27) is listed amongst the “TUW Under 30”, a list of selected TU Wien students and employees. Similar to the” Forbes Under 30”, this list features young and extraordinary researchers and entrepreneurs from the TUW, being able to present exceptional achievements in their area of research. Giulia graduated in nuclear physics and is doing her PhD at the Security& Privacy Research Group of Matteo Maffei. She specializes on Blockchain-protocols and is currently working on a blockchain bridge called “Glimpse”, enabling cross-currency transaction between Krypto-currencies. Giulia presented her results at the renowned IT conference USENIX Security Symposium. For more details see the article featured in the current print issue of the TUW Magazine #02-2023 “Schwerpunkt: Under 30” (pages 26-28) and also her bio online .
2023-10-12
Achievement
Sophie Rain listed amongst Top 30 @ TU Wien Under 30.
Sophie Rain (28) is amongst the “TUW Under 30” in 2023, a list of selected TU Wien students and employees. Similar to the “Forbes Under 30”, this list features young and extraordinary researchers and entrepreneurs from the TUW, being able to present exceptional achievements in their area of research. Sophie is a PhD student in Laura Kovacs’ Research Unit of Formal Methods in Systems Engineering. Her work focuses on the security verification of Blockchain applications by applying mathematical concepts such as game theory, logic and most importantly automated reasoning. Her work was presented at major security conferences such as CAV 2021 and CSF 2023. Furthermore, she is leading the TU Wien initiative “Abenteuer Informatik für Volksschule”, organizing workshops for pupils. For more details see the article featured in the current print issue of the TUW Magazine #02-2023 “Schwerpunkt: Under 30” and also her bio online .
2023-10-09
Public Lecture
Daniel Gruss gave a talk on “Sustainable Security.“
The talk is a part of the Public Lecture Series ‘Sustainability in Computer Science’ under the auspices of Informatik Austria . This lecture series, a pioneering initiative in Austria, unites all Austrian CS departments and faculties to emphasize the vital role of sustainability in computer science. It showcases research solutions for real-world challenges and inspires progress towards a sustainable future.
Abstract. Global ICT electricity consumption is already beyond 11 percent of the worldwide electricity production and still increasing. By 2030 it may reach around 25 percent. Previous approaches to improve efficiency and performance have often sacrificed security, leading to disastrous security issues like Meltdown and Spectre. Patching just these two vulnerabilities increases power consumption on affected computers by a seemingly harmless 5 percent. By 2030, this may be more than 1 percent of the global electricity production by just a single out of thousands of patches. This development is not sustainable, and in this talk, we will discuss both the problem and potential revolutionary solutions."
2023-10-01
Outreach to society
Why Data Protection Is Important and How It Succeeds
Martina Lindorfer delivered a moderated talk , discussing the critical importance of data protection, privacy, and IT security at Vienna Humanities Festival.
September 2023
2023-09-20 Outreach to society
Johanna Ullrich was an invited speaker at the International Digital Security Forum (IDSF ) held in Vienna. She participated in a high-level panel discussion titled “Securing the Energy Sector: Strategies for Building Resilience against Cyber Attacks,” where she delivered an insightful presentation focused on strengthening cybersecurity and resilience within critical energy infrastructure.
2023-09-15
Research Visit
Lecture by Marco Mellia (Politecnico di Torino) “Data, AI and Cybersecurity - a possible cocktail?”
Abstract: Modern Artificial Intelligence technologies, led by Deep Learning, have gained unprecedented momentum over the past decade. Following this wave of “AI summer”, the network research community has also embraced AI/ML algorithms to address many problems related to network operations, management and cybersecurity. This talk will give an overview of some of the recent results in applying AI-based solution to automatically process traffic traces and detect novel attacks, prevent cybersquatting attacks, support forensic investigations, and open new opportunities to protect users from possible abuses.
Bio: Marco Mellia is a full professor at Politecnico di Torino, Italy, where he is the coordinator of the SmartData@PoliTO center on Big Data, Machine Learning and Data Science. His research interests are in the area of Internet monitoring, users’ characterisation, cyber security, and big data analytics applied to different areas. He has co-authored over 250 papers published in international journals and presented in leading conferences. He won the IRTF ANR Prize at IETF-88, and best paper award at IEEE P2P’12, ACM CoNEXT’13, IEEE ICDCS’15. He is Fellow of IEEE and Editor in Chief of the Proceedings of the ACM on Networking.
2023-09-14 Outreach to society
The TU Wien cryptography expert Prof. Elena Andreeva was featured in the Puls4 documentary Angriff aus dem Internet (Attack from the Internet).
Prof. Andreeva opens the doors to her research space and group at TU Wien, explaining the role of cryptography in today’s digital world. She also discusses how everyday devices like mobile phones can be vulnerable to cyber attacks.
The documentary sheds light on the importance of preventing cyber attacks, given their ubiquitous growth worldwide, and more specifically, in Austria. As the attackers range from criminals to state-run organizations, the targets vary from public administration and states to critical infrastructure and, not least, private individuals. The documentary presents several cyber attacks and discusses directions for prevention.
The interview with Elena Andreeva is available for reading in TU Wien Informatics News.
2023-09-04 Summer School
Graz Security Week 2023 , organized by the Institute of Applied Information Processing and Communication (IAIK) at Graz University of Technology, is set to take place. This event is specifically tailored for graduate students who are enthusiastic about delving into the intricacies of security and correctness in computing devices. The school will cover a diverse range of topics, including Runtime Security, Side-Channels, Privacy, Secure Cryptographic Implementations, and Security Verification. It offers a unique opportunity for participants to deepen their knowledge and engage in discussions surrounding these critical aspects of computer security.
August 2023
2023-08-03
Research Visit
Lecture by Yossi Oren (Ben Gurion University of the Negev) “Targeted Deanonymization via the Cache Side Channel: Attacks and Defenses”
Location: TU Graz, IAIK seminar room (IFEG042), Inffeldgasse 16a
Time: 13:00 – 14:00
Abstract: Side-channel techniques have been traditionally applied toward the recovery of computer-related secrets, such as cryptographic keys. Recently, however, attackers have turned to target humans, who also share secrets of their own with their computers. Recoverable human secrets include, for example, browsing habits, keystrokes, political or religious beliefs, or sensitive information about the user’s health. In this talk, I will show how a cache side-channel attacker can target humans using a targeted deanonymization attack. Targeted deanonymization attacks, which let a malicious website discover whether a website visitor bears a certain public identifier, such as an email address or a Twitter handle, are both practical and dangerous, as they can put journalists, activists, and other vulnerable populations into serious risk.
After describing and demonstrating the attack, I will talk about the unique challenge of defending against an attack which involves users, and show how mitigations against the attack were built into the popular NoScript extension.
Based on joint work with Mojtaba Zaheri and Reza Curtmola presented at USENIX Security ’22. Artifacts available here: https://github.com/leakuidatorplusteam/artifacts
Bio: Yossi Oren is a Senior Lecturer (Assistant Professor in U.S. terms) in the Department of Software and Information Systems Engineering at Ben Gurion University of the Negev, and a member of BGU’s Cyber Security Research Center. Prior to joining BGU, Yossi was a Post-Doctoral Research Scientist in the Network Security Lab at Columbia University in the City of New York and a member of the security lab at Samsung Research Israel. He holds a Ph.D. in Electrical Engineering from Tel-Aviv University (thesis), and an M.Sc. in Computer Science from the Weizmann Institute of Science (thesis). His research interests include implementation security (side-channel attacks, micro-architectural attacks, power analysis and other hardware attacks and countermeasures; low-resource cryptographic constructions for lightweight computers) and cryptography in the real world (consumer and voter privacy in the digital era; web application security). He has been recognized by The Register as a Top Boffin.
July 2023
2023-07-14
Award
Most Influential DIMVA Paper 2014-2018 Award
The Most Influential DIMVA Paper Award for the period 2014–2018 has been awarded to Daniel Gruss, Clémentine Maurice, Klaus Wagner, and Stefan Mangard for their groundbreaking paper “Flush+Flush: A Fast and Stealthy Cache Attack .” The work represents a major milestone in research on microarchitectural side-channel attacks. Earlier research had demonstrated that CPU caches can leak sensitive information and that cache attacks can often be detected by monitoring cache hits and misses using hardware performance counters. However, this paper fundamentally challenged that assumption.
The authors introduced the novel Flush+Flush attack, a technique that relies solely on measuring the execution time of the CPU flush instruction to determine whether data is cached. Unlike previous cache attacks, Flush+Flush performs no memory accesses, which means it generates virtually no cache misses and minimizes cache hits. As a result, the attack is significantly harder to detect using existing monitoring techniques.
Beyond its stealth properties, the Flush+Flush attack also demonstrated superior performance. The authors achieved data transmission speeds of up to 496 KB/s in a cross-core covert channel, making it approximately 6.7 times faster than previously known cache covert channels at the time.
The paper has had a lasting impact on the field of hardware security, influencing both academic research and practical approaches to detecting microarchitectural attacks. The recognition as the Most Influential DIMVA Paper highlights its continued relevance and importance to the security research community.
2023-07-11
Research Visit
Lecture by Mathieu Jan (CEA LIST) “Formal Hardware/Software Modeling for Timing Properties: from Safety to Security”
Location: TU Graz, IAIK seminar room (IFEG042), Inffeldgasse 16a
Time: 10:00 – 11:00
Abstract: The emergence of open hardware initiatives, for instance, based on the RISC-V ISA, exposes more easily the exact behavior of hardware designs. They can then be analyzed and combined with application-level semantics to formally verify complex safety (and security) properties at the system level. In this talk, we first present an overview of the LEAF approach for verifying such timing-related properties. Then, we focus on the required formal model tailored to a specific property: the detection of Timing Anomalies (TA) within pipelines of processors. A TA is a counterintuitive timing behavior that can threaten Worst-Case Execution Time (WCET) analyses. We also report ongoing work to generate such pipeline formal models from RISC-V processors described in Chisel/FIRRTL. Finally, we conclude on current extensions to apply the LEAF approach to safety properties.
Bio: Dr. Mathieu Jan obtained his engineering diploma in 2003 and got a Ph.D. in 2006 on data management for grid architectures from Univ. of Rennes 1 in an INRIA laboratory. He joined CEA LIST in 2007 as a full-time researcher. Since then, his main research interests are embedded systems and real-time systems. Senior expert at CEA LIST since 2014, he obtained a “Habilitation à Diriger des Recherches” (HDR) in 2016, and is a CEA Research Director since 2021. He spent the whole year 2019 as visiting scholar at the University of California, Berkeley (UCB) in the group of Prof. Edward Lee. Since 2020, Mathieu focuses on the hardware/software formal verification of embedded systems and is the Ph.D. director of several Ph.D. students in this area.
2023-07-07
Talk
Martina Lindorfer is a speaker and a mentor at EPFL School of Computer and Communication Sciences Summer Research Institute
Martina Lindorfer delivered a talk titled “Watching the Watchmen - Shedding Light on Data Collection in Mobile Apps” at The Summer Research Institute (SuRI), held at the École polytechnique fédérale de Lausanne in Switzerland.
2023-07-05
Research Visit
Lecture by Jean-Max Dutertre (École des Mines de Saint-Étienne) “Review of laser and EM fault injection attacks into microcontrollers”
Location: TU Graz, IAIK seminar room (IFEG042), Inffeldgasse 16a
Time: 14:00 – 15:00
Abstract: Microcontrollers storing valuable data or using security functions are vulnerable to fault injection attacks. Among the various types of faults, instruction skips induced at runtime proved to be effective against identification routines or encryption algorithms. Until recently, most research papers assessed a fault model that consists in a single instruction skip, i.e. the ability to prevent one chosen instruction in a program from being executed. This seminar reports experimental results that extend the complexity and versatility of the instruction-skip fault model. It shows how using laser or EM fault injection makes it possible to induce several consecutive instructions skips or to skip instructions from different parts of a program. It focuses on results obtained on custom test circuits and general purpose microcontrollers at different technology nodes. An analysis of the involved injection mechanisms is also provided.
Bio: Dr. Mathieu Jan obtained his engineering diploma in 2003 and got a Ph.D. in 2006 on data management for grid architectures from Univ. of Rennes 1 in an INRIA laboratory. He joined CEA LIST in 2007 as a full-time researcher. Since then, his main research interests are embedded systems and real-time systems. Senior expert at CEA LIST since 2014, he obtained a “Habilitation à Diriger des Recherches” (HDR) in 2016, and is a CEA Research Director since 2021. He spent the whole year 2019 as visiting scholar at the University of California, Berkeley (UCB) in the group of Prof. Edward Lee. Since 2020, Mathieu focuses on the hardware/software formal verification of embedded systems and is the Ph.D. director of several Ph.D. students in this area.
June 2023
2023-06-28
Research Visit
Lecture by Kenneth Paterson (ETH Zurich) “Cryptography in the Wild.”
Abstract: In this talk I’ll discuss a research theme that has emerged in the last few years, namely the analysis of deployed cryptographic systems. There is a small but dedicated group of researchers who do this kind of work. I’ll reflect on how we conduct this kind of research, why we do it, and what we can learn from it about how developers use (and abuse) cryptography.
Bio: Kenneth Paterson is a Professor of Computer Science at ETH Zurich, where he leads the Applied Cryptography Group and is currently the head of department. He was Program Chair for Eurocrypt 2011 and Editor-in-Chief of the Journal of Cryptology from 2017 to 2020. He co-founded the Real World Cryptography series of conferences. His research has won best paper awards at conferences including ACM CCS 2016, 2022, IEEE S&P 2022, 2023, NDSS 2012, CHES 2018, and IMC 2018. He was made a Fellow of the IACR in 2017. In 2022, he was winner of the Golden Owl best teaching award for the Department of Computer Science at ETH.
2023-06-26
Presentation
Giulia Scaffino presented “Glimpse“ at the the prestigious “USENIX Security Symposium“
Glimpse stands out as an innovative protocol, facilitating secure cross-chain token transfers in a fully decentralized manner, eliminating the need for large commercial crypto-depots. This accomplishment is the result of collaborative efforts by Giulia Scaffino, Lukas Aumayr, Zeta Avarikioti, and Matteo Maffei.
Notably, the Glimpse protocol is compatible with blockchains that have limited scripting languages. The authors provide a specific implementation of Glimpse for the Liquid Network, a Bitcoin pegged sidechain. The protocol’s security is proven within the Universal Composability (UC) framework, instilling a high level of confidence in its security guarantees. The researchers conducted an economic analysis of the Glimpse protocol, revealing that verifying a simple transaction on Bitcoin-like chains using Glimpse incurs a maximum of 700 bytes of on-chain overhead, resulting in a one-time fee of $3. This fee is only twice as much as a standard Bitcoin transaction, highlighting the cost efficiency of Glimpse. Overall, the presented advancements unlock exciting possibilities for the world of cryptocurrencies.
2023-06-21
Research Visit
Lecture by Christian Cachin (ETH Zurich University of Bern) “Consensus in blockchains: Overview and recent results.”
Abstract: Reaching consensus despite faulty or corrupted nodes is a central question in distributed computing; it has received renewed attention over the last years because of its importance for cryptocurrencies and blockchain networks. Modern consensus protocols in this space have relied on a number of different methods for the nodes to influence protocol decisions. Such assumptions include (1) traditional voting, where each node has one vote, (2) weighted voting, where voting power is proportional to stake in an underlying asset, and (3) proof-of-X, which demonstrates a cryptographically verifiable investment of a resource X, such as storage space, time waited, or computational work. This talk will give an overview of blockchain consensus methods and then highlight recent work on constructing new consensus protocols and analyzing existing ones.
Bio: Christian Cachin is a professor of computer science at the University of Bern, where he has been leading the Cryptology and Data Security Research Group since 2019. Prior to that he worked for IBM Research - Zurich for more than 20 years. He has held visiting positions at MIT and at EPFL and has taught at several universities during his career in industrial research. He graduated with a Ph.D. in Computer Science from ETH Zurich in 1997. He is an IACR Fellow, ACM Fellow, IEEE Fellow, recipient of multiple IBM Outstanding Technical Achievement Awards, and has also served as the President of the International Association for Cryptologic Research (IACR) from 2014-2019. With a background in cryptography, he is interested in all aspects of security in distributed systems and especially in cryptographic protocols, consistency, consensus, blockchains, and cloud-computing security. He is known for developing cryptographic protocols, particularly for achieving consensus and for executing distributed cryptographic operations over the Internet. In the area of cloud computing, he has contributed to standards in storage security and developed protocols for key management. He has co-authored a textbook on distributed computing titled Introduction to Reliable and Secure Distributed Programming. While at IBM Research he made essential contributions to the development of Hyperledger Fabric, a blockchain platform aimed at business use.
2023-06-19
Research Seminar
Verification of Game-Theoretic Security Properties for Blockchain Protocols
2023-06-14
Research Visit
Lecture by Katharina Krombholz (CISPA Helmholtz Center for Information Security) “Towards Understandable Privacy and Security Guarantees - The Human Factors Perspective.”
Abstract: Due to the digitization of everyday things, humans and their surroundings are exposed to visible and invisible computers that continuously collect and share data. As a result, it is almost impossible for users and bystanders to understand these complex data sharing models along with their implications for privacy. In this talk, I will present current trends in human-centric privacy research along with a series of lessons learned to make privacy understandable and effective for everyone.
Bio: Katharina Krombholz is a tenured faculty at the CISPA Helmholtz Center for Information Security in Saarbrücken, Germany, where she leads the usable security research group. She is PC co-chair of SOUPS 23 and 24 and active in both the security & privacy and human-computer interaction communities. Katharina Krombholz obtained her PhD from TU Wien and has been visiting researcher/faculty at various institutions around the world, including LUMS in Lahore and NII in Japan.
2023-06-05
Outreach to society
Daniel Gruss and Martina Lindorfer are the speakers at the Austrian Computer Science Day
Daniel Gruss: Security – Can we afford to have it? Can we afford not to have it?
Martina Lindorfer: Watching the Watchmen – Shedding Light on Data Collection in Mobile Apps.
May 2023
2023-05-31
Research Visit
Lecture by Mooly Sagiv (Tel Aviv University) “Scaling Formal Verification to Realistic Code with Applications to DeFi Verification.”
Abstract: Deductive verification tools like Dafny and Viper compile the program into an SMT formula and then utilize SMT solvers to find potential bugs or prove their absence. These tools are used to reason about small programs. However, these techniques do not scale due to the inherent complexity of SMT solving and the need to specify exact procedure behavior. Furthermore, common coding patterns such as nonlinear expressions, unbounded data structures and indirect storage complicates SMT reasoning. We present the Certora Prover, a tool that checks the semantics of the executable code against its intended behavior written in a high-level declarative language for writing relational specifications, called CVL. Developer-written specifications in CVL have prevented billion-dollar mistakes and improved code security. The Certora Prover has secured 50% of the total value locked in the Ethereum blockchain. Also, specifications are written by Solidity developers and external security experts.
Bio: Mooly Sagiv is Full Professor, Chair of Software Systems School of Computer Science, Tel Aviv University, Israel. He is a recipient of an ERC Advanced Grant 2013. He is also the CEO of Certora, a startup company providing formal verification of smart contracts. His research focuses on easing the task of developing reliable and efficient software systems. He is particularly interested in static program analysis which combines two disciplines: automated theorem proving and abstract interpretation. In the next decade, I am hoping to develop useful techniques in order to change the ways modern software is built. I am particularly interested in proof automation, given a program and a requirement, automatically prove or disprove that all executions of the program satisfying the requirements. He is interested in developing practical solutions to proof-automation by: (i) exploring modularity of the system and (ii) relying on semi-automatic and interactive processes, where the user manually and interactively guides the proof automation, and (iii) simplifying the verification task by using domain-specific abstractions expressed in a decidable logic. He is applying these techniques to verify safety of liveness of distributed systems.
2023-05-22
Research Seminar
PYTHIA: Supercharging Parallel Smart Contract Execution with the help of Optimistic Predictions
2023-05-03
Research Visit
Lecture by Konrad Rieck (TU Berlin) “When Papers Choose their Reviewers: Adversarial Machine Learning in Conference Management Systems.”
Abstract: The number of papers submitted to scientific conferences is steadily rising in many disciplines. To handle this growth, systems for automatic paper-reviewer assignments are increasingly used during the reviewing process. These systems employ statistical topic models to characterize the papers’ content and automate their assignment to reviewers. In this talk, we investigate the security of this automation and introduce a new attack that modifies a given paper so that it selects its own reviewers. Our attack is based on a novel optimization strategy that fools the topic model with unobtrusive changes to the paper’s content. In an empirical evaluation with a (simulated) conference, our attack successfully selects and removes reviewers, while the tampered papers remain plausible and often indistinguishable from innocuous submissions.
Bio: Konrad Rieck is a professor at TU Berlin, where he leads the Chair of Machine Learning and Security as part of the Berlin Institute for the Foundations of Learning and Data. Previously, he held academic positions at TU Braunschweig, the University of Göttingen, and Fraunhofer Institute FIRST. His research focuses on the intersection of computer security and machine learning. He has published over 100 papers in this area and serves on the PCs of the top security conferences (system security circus). He has been awarded the CAST/GI Dissertation Award, a Google Faculty Award, and an ERC Consolidator Grant.
April 2023
2023-04-19
Research Visit
Lecture by Alessandro Abate (University of Oxford) “Logic meets Learning - Formal Synthesis with Neural Templates.”
Abstract: I shall present recent work on CEGIS, a “counterexample-guided inductive synthesis” framework for sound synthesis tasks that are relevant for dynamical models, control problems, and software programs. The inductive synthesis framework comprises the interaction of two components, a learner and a verifier. The learner trains a neural template on finite samples. The verifier soundly validates the candidates trained by the learner, by means of calls to a SAT-modulo-theory solver. Whenever the candidate is not valid, SMT-generated counter-examples are passed to the learner for further training. I shall elucidate the ins & outs of the CEGIS framework, and display its workings on a few problems: synthesis of Lyapunov functions and of barrier certificates; hybridisation of nonlinear dynamics for safety verification; synthesis of digital controllers for continuous plants; and an application in real-time autonomy.
Bio: Alessandro Abate is Professor of Verification and Control in the Department of Computer Science at the University of Oxford, where he is also Deputy Head of Department. Earlier, he did research at Stanford University and at SRI International, and was an Assistant Professor at the Delft Center for Systems and Control, TU Delft. He received an MS/PhD from the University of Padova and UC Berkeley. His research interests lie on the formal verification and control of stochastic hybrid systems, and in their applications in cyber-physical systems, particularly involving safety criticality and energy. He blends in techniques from machine learning and AI, such as Bayesian inference, reinforcement learning, and game theory.
2023-04-18 Kick-off event
On April 18, the Technical University of Vienna (TUW) hosted the highly anticipated kick-off event of SPyCoDe, a groundbreaking research program focused on the Semantic and Cryptographic Foundations of Security and Privacy through Composite Design. Generously funded by the Austrian Science Fund (FWF), this initiative aims to delve into the complexities of security and privacy in the digital landscape. The event successfully brought together a diverse group of project participants, fostering an atmosphere of collaboration and innovation.
The presentation of the SPyCoDe program covered its purpose, methodology, research plans, 14 projects, and expected results. It captivated not only the students but also garnered approval from esteemed members of the Advisory Board, including Prof. Véronique Cortier (French National Scientific Research Center (CNRS)), Prof. Bart Preneel (Research group COSIC, KU Leuven), and Prof. Christoph Paar (Ruhr-Universität Bochum). The ensuing discussion proved fruitful, providing invaluable insights and advice crucial to the program’s success in achieving its goals.
Throughout the day, participants seized the opportunity to connect with one another, engaging in informal conversations, knowledge exchange, and thought-provoking discussions. These interactions delved into the complex topics underlying the research activities of the program. A series of cross-cutting sessions facilitated collaborative efforts between the PIs and students, fostering interdisciplinary cooperation and kick-starting joint research. These sessions focused on studying various aspects of security analysis, compositionality, reasoning, and other pertinent subjects, fostering intensive and illuminating dialogue.
The Kickoff event marked a promising beginning for the SPyCoDe research program, which aims to shed light on the intricate world of security and privacy in the digital realm. With a diverse array of projects and a dedicated team of researchers, the program is poised to make significant strides in advancing our understanding and addressing the challenges of this ever-evolving field.